This page aims to help users, who are infected by DecryptorMax ransomware. Please, use the guide below to decrypt DecryptorMax files and to restore the original ones
This is malicious software known as trojan-ransomware. If contracted, eradicate DecryptorMax immediately. The malware goes to work in Windows files and drivers to encrypt personal files for which a key is offered in return for a ransom payment. There is a decryption key available, created by Fabian Wosar of Emsisoft (a link is provided below). Even with this good news, it must be remembered that there are other security concerns as a result of infection that make it important to remove DecryptorMax at the earliest chance. The presence of such malware in a system can leave a back-door open for further infection, and as this encryption now has a key, the author could decide to launch another, different follow-up attack. This could be a more effective form of ransomware, or malware employing key-logging or screenshots that could result in direct financial/data loss or I.D theft. Discovered first in November 2015, this infection is also know as CryptInfinite ransomware.
There a a few different ways that this infection can find its way into a system, though this one is commonly disguised as a Résumé (C.V) that is a Word attachment with the trojan hidden as a piece of active text (or a Macro) that executes the malware if opened. This method supports the growing professional opinion that this and other ransomware are now specifically targeting small-to-medium-sized businesses (SMB) in the same way that CryptoWall and TorrentLocker did last year (SMB accounted for almost half the victims of these two infections).
Perhaps the hackers are taking advantage of company networks where employees assume that workplace software security will filter any threats, and the authors use this vulnerability to efficiently spread the malware. The Résumé scam seems to support this, as well as the observation that increasingly, spam ‘mail runs are being launched mainly between 09.00 and 13.00 and adjusted for the time zone of the target. This is unsurprising because after all, ransomware is big business – the two attacks last year are estimated to have raised in excess of US$ 30m for the criminals.
For private users, there are many social engineering ruses being devised, like notifications of one kind or another which appear to be from government offices or shipping and postal companies. To stop DecryptorMax and similar infections, it is important not to open unsolicited ‘mail – especially if it is seen to contain an attachment. The other methods of contracting the ransomware are: the download and unsupervised installing of freeware or pay-per-install bundles containing the trojan; by clicking fake pop-ups offering freeware updates or virus scans; on unverified torrent-share ‘sites; on either compromised legitimate ‘sites or those hosted by hackers, and falling victim to an exploitation kit attack; through a manual hack via an unsecured network connection, or caught from external devices which have been unwittingly infected. It should be clear now, knowing these avenues of attack – all ransomware infections can be avoided.
Detecting and dealing with DecryptorMax
When encryption is finished the desktop wallpaper will be replaced with a ransom note, though if the bug can be discovered earlier, it will cause less work and minimize risks of a subsequent breach. As with other variants, this one is good at hiding from all but the most rigorous and targeted of security applications. For this reason, users should be wary of the visible signs of malware in the system. Encryption takes a great deal of processing power, so the CPU is drained significantly. Users should notice a slowing of normal operating speeds, possibly with some applications crashing mid-process. This may be accompanied by momentary and random freezing of the display.
Unprompted internet connection should be noticeable as the bug tries to communicate with its server, an unusual amount of traffic at ports will be detected, and pop-ups and spam will increase. If any such behavior is present, then disconnect or disable all networks and internet connections both wired and wireless. Check personal files for any that are encoded – they will have extensions changed to .crinf (hence the alternative name, CryptInfinite). Place any corrupted files in a new folder, and as a precaution, back-up clean files to an external storage such as a pen drive or disk. If the user has available backed-up files, then it’s possible to simply delete DecryptorMax (instructions follow) and then to re-install the back-ups. If there are no backup files, it is necessary to download the decryption software for recovery. Note: this ransomware deletes Shadow Volumes and disables Start-up Restore to prevent files being restored from these recovery vectors. Be sure to get rid of DecryptorMax completely before starting file recovery.
How to decrypt DecryptorMax encrypted files
To successfully decrypt DecryptorMax files, please follow the steps below. Try to perform the actions as strictly as possible. You need one pair of encrypted and original file, in order to generate a decryption key.
Step 1: Download the DecryptorMax free decryption utility from there: http://emsi.at/DecryptCryptInfinite
Step 2: Drag-and-drop an encrypted file and his original at the decrypt_cryptinfinite.exe file.
Important!!! You must select both the encrypted and unencrypted version of a file and drag them both onto the decrypt_cryptinfinite.exe executable!
Step 3: Next, a User Account Control window will appear. Click OK.
Step 4: On the next screen, you will have 2 options for the e-mail of the ransom note. Please select either 1 or 2 (the one that contains the associated email addresses for your encryption).

Step 5: The program will start the bruteforce process for determining the decryption key. This may take long, so please, be patient.
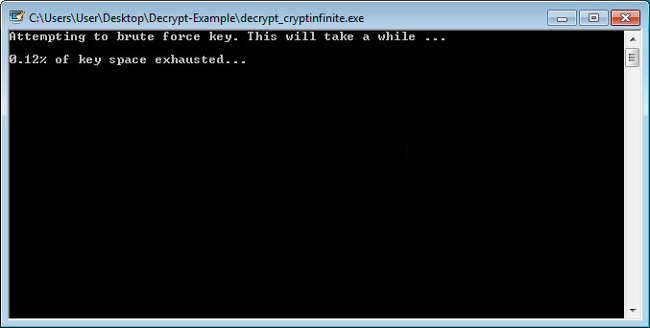
Step 6: When the bruteforce process is done and the decryption key is found, you will see a screen like this below:
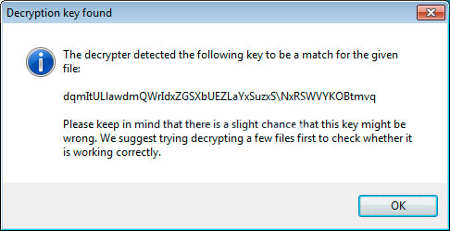
Step 7: Click the OK button at the window. The real decryption process will start. When you see a License agreement, please click Yes.

Step 8: Click Add Folder to add a folder with encrypted files. Add as many folders as you need. When finished with adding folders click Decrypt. All of your files should now be decrypted.
How to prevent DecryptorMax
So now the computer is clean; with a little setting up and a careful working routine it can remain so. For insurance, make very regular file back-ups and store in Cloud, or on a disconnected external drive/device. Think about the ways into the system detailed above. Think of what can be done technically to defend these pathways, and new ways of working to patch any user-caused vulnerabilities. Don’t open unsolicited or unexpected ‘mail, however inviting or convincing it may appear – and switch off ActiveX setting for Microsoft Office applications. When downloading, go directly to the author’s website for freeware and even then, examine the file for any additions using Advance install. Avoid pop-ups. Always keep browsers current with the latest version and turn on all available warning features. Patch operating systems with all updates and check regularly for these. Installing an advanced firewall will protect against infiltration. If the trojan-ransomware does get in somehow it can prevent it running by disallowing communication to the control server (place settings to disallow communication with the Tor and I2P networks and limit ports to authorized use only). Extortion-ware can also be disabled in the system by altering Administrator and Privilege settings to disallow .exe files running on certain registry paths – DecryptorMax uses the %AppData% and %UserProfile% folders – see windows.microsoft.com for more details on this. A good security application to perform regular scans will give the user another layer of safety.
DecryptorMax isn’t a maximal problem, though system safety is of maximum importance – the next variant to come onto the market might not be so easy to deal with!

