The focus of this article is a win-locker called Zepto virus. It falls under the category of ransomware. The virus assigns a 16-digit identification number to each victim. Zepto ransomware is one of the more recent win-lockers. It does not present itself with a given name. Security experts have chosen the name Zepto virus to refer to the program. Zepto is the custom suffix the win-locker appends to each file it encrypts. Upon observing the virus’s specifications, researchers have discovered that it is not a unique program. Zepto ransomware is a rehashed version of AutoLocky ransomware. This virus was already reworked once. An earlier name for it is Locky ransomware.
Zepto virus uses two types of technologies to conduct the encryption process. The RSA-2048 public key allows the clandestine program to encrypt all vulnerable files on the hard drive. The AES 128-bit cipher is used to create the private key, required for decrypting. The hackers store the key on a remote server.
Zepto ransomware can encrypt different file types. It targets the most commonly used formats. Text documents, images, audios, videos, archives, databases, spreadsheets, presentations and compressed folders are all vulnerable. To put things into perspective, the number of vulnerable file types is 142. Adding a custom extension is not the only change Zepto virus does to the title of the encrypted file. The malicious program gives it a different name altogether. It uses hexadecimal characters from the victim’s ID to generate a custom 32-digit name.
Upon completing the encryption, Zepto ransomware informs the victim of its actions. Unlike other malware, win-lockers announce their presence. This is a necessity. The virus needs users to cooperate by paying the ransom. Keeping you oblivious to its presence would be no good. You do not need to look for symptoms to detect a win-locker. Zepto virus creates a folder and a ransom note to inform the user of its presence. The folder is called enc. The virus places it in the C: hard drive.
Zepto ransomware names the ransom note _72_HELP_instructions.html. The file lists the demands of the cyber criminals and explains how to complete the payment. The required sum is 0.5 BTC. This amounts to $338.87 USD, according to the current exchange rate. Bitcoins are the usual choice for ransomware because they guarantee the anonymity of the recipient. To transfer the sum, the victim can use one of two links from the ransom note. If they happen to be unavailable, he can download the Tor browser and load a payment page in it. Similar to bitcoin platforms, the Tor browser protects people’s anonymity.
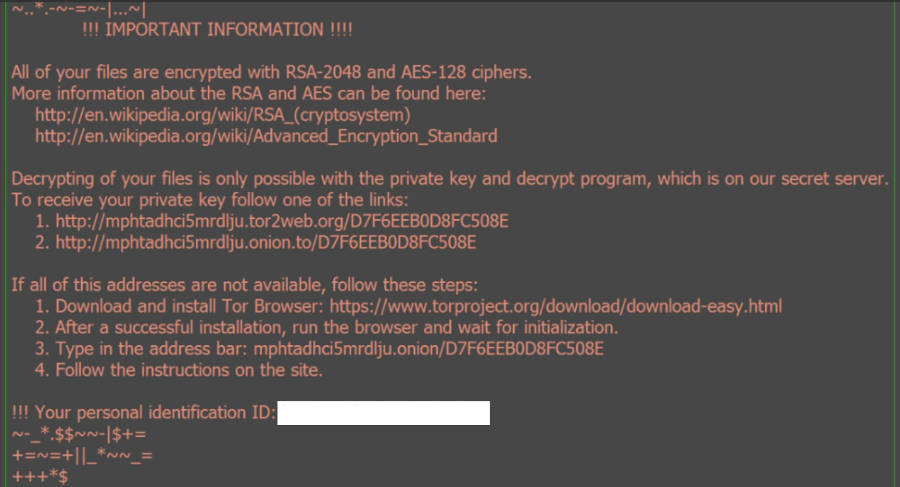
Like a lot of other win-lockers, Zepto virus tries to make people believe their issue can only be resolved by paying the ransom. Trusting a group of cyber criminals is never a good idea. They may not make good on their promise and keep your files locked. Even if they provide the decryption key, there is no guarantee that there will not be another attack. The win-locker can make registry entries and install itself all over again.
Knowing how a virus can gain entry into your machine can help you ward off an invasion. Zepto virus uses the most common distribution technique for infections of this kind. It travels through spam e-mails. According to recent reports, there has been a surge in the spam campaigns in the past week. At the end of June, there was an influx of over 130,000 e-mails in just four days.
There has been a slight change in the format of the spam e-mails, spreading Zepto ransomware. They have become more diverse. Up until last week, the nefarious program was spread through e-mails with a specific format. The subject of the message was “ATTN: Invoice J-[RANDOM NUMBERS]”. A Microsoft document contained the infection. When opened, the user would see an incomprehensible text. There would be a message, asking him to run a macro to make the text readable. Doing so would open the door for Zepto ransomware. Knowing this penetration algorithm could help you, as there can still be spam letters with this specific title.
The insidious program has started using more diverse messages. A single format cannot suffice for a virus with a high distribution rate. Users would get to know about it and recognize the bogus e-mails. People have started to contact Zepto virus through different e-mails. The general idea of the message is still the same. It talks about an important document, like an invoice, a receipt, a letter or a notice. It urges the user to get acquainted with it as soon as possible. The host file is a zip archive. The new convention uses a certain format for the document. The file name encompasses the recipient’s account user name, an underscore and a random number. By now, Zepto ransomware uses malicious Javascript for its distribution. Researchers have uncovered over 3,300 .js samples.
To distinguish spam from reliable messages, check the sender’s data. Look up the e-mail address. If the letter has been sent on behalf of a certain entity, the e-mail account should match their official contacts. In case you have doubts, you can contact the organization in question. You should never trust e-mails from unconfirmed senders.
Removing a ransomware program is a difficult task. These infections make registry entries and create files in various directories to prevent being deleted completely. If you do not eliminate all corrupted data, Zepto virus can get installed to your system again at a future point. You will need to use a professional antivirus program to uninstall the win-locker. A full removal guide is located below.
Video on Zepto Virus
Remove Zepto File Virus
Method 1: Restore your files encrypted by Zepto virus using ShadowExplorer
Usually, Zepto ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files encrypted by Zepto virus using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Zepto ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

