I wrote this article to help you remove Sanctions Ransomware. This Sanctions Ransomware removal guide works for all Windows versions.
Sanctions ransomware is a win-locker which first appeared in early 2016. About a year later, another build of the malignant program was released. The purpose of this virus is to get victims to pay the developers behind it. The infection spreads throughout the hard drive, targeting vulnerable file types. Sanctions ransomware targets 97 formats. It encrypts files using a combination of two algorithms, AES-256 and RSA-2048. It appends the .wallet suffix to the names of the infected objects. This is a reference to the requirement the victim has to meet.
The cyber criminals behind Sanctions ransomware demand a certain payment in exchange for the unique decryption key. The ransom has to be paid in Bitcoins. The hackers have opened a Bitcoin wallet for accepting the payments. They have chosen this cryptocurrency because it is the safest. The platforms for trading Bitcoins do not require users to enter personal details when creating an account. Furthermore, the transactions cannot be traced. The crooks can withdraw funds and send them to a bank account without risking to get caught.
If you are wondering how Sanctions ransomware was able to gain access to your system, we can elaborate. The covert program travels in spam emails. The executable of the win-locker gets merged with an attachment. The fake messages carrying the infection can vary in topic. The sender can talk about a delivery package, a prize, a bill, a fine, a court order or something else your would consider important. The file will be listed as a document which contains details on the matter. This is how spammers trick people into opening the host for the virus. To check whether a given email is legit, proof the sender’s contacts. If he has written on behalf of a certain organization, the contacts should match. You can go to the official website of the entity in question and check the details listed there.
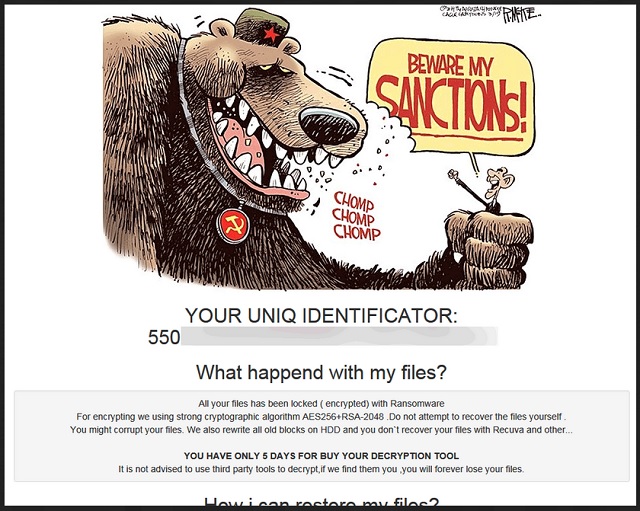
Sanctions ransomware gets installed on the background which makes it difficult to notice. Both the installation and the encryption take a small amount of time, so you may be unable to react. After the win-locker has finished locking files, it drops a ransom note to notify the victim about the event. The file, titled RESTORE_ALL_DATA.html, is saved to the desktop. Apart from the trivial message, the document contains a caricature. It depicts a bear wearing Soviet national symbols which is holding a man hostage. The person is threatening with sanctions, but his actions seem to have no effect on the situation. This is an allegory, describing the relations between Russian and the USA. We know for a fact that the win-locker has been developed by Russian hackers.
The cyber criminals explain that their win-locker has enciphered the vulnerable files on your system and rewritten all old blocks of your HDD. As the message further elaborates, the latter operation was done to eliminate the possibility of recovering files with the help of auxiliary utilities. The attackers insist that the only way to restore the lost data is with the decryption tool they have devised for the purpose. They give victims 5 days to pay the whooping ransom of 6 BTC. According to the current exchange rate, this sum converts to about $6,790 USD. This is one of the highest ransoms to date.
Imagine paying the hackers behind Sanctions ransomware and not having the issue settled. This is within the realm of possibility. The renegade developers could collect the ransom and refuse to send you the decryption tool. Another possible scenario is for the win-locker to launch a second attack in time. This is possible because the terms “decryption” and “removal” are not synonymous. The rogue program will remain on your hard drive after the decryption tool has finished unlocking your files. Since the hackers use a command and control (C&C) server to control the win-locker remotely, they can launch another attack in time.
As with all encryption viruses, malware experts are working on a custom decryptor for Sanctions ransomware. While you may not be able to view your files until a working decryptor is created, you will not lose them. Sanctions ransomware does not delete the infected objects when the deadline for paying expires. You can still try to recover your data by using the tools listed below. If the insidious program has not deleted the shadow volume copies of your files, you may be able to recover them.
Sanctions Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, Sanctions Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Sanctions Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

