I wrote this article to help you remove RobinHood Ransomware. This RobinHood Ransomware removal guide works for all Windows versions.
RobinHood ransomware is a deceptive win-locker. The developers of the nefarious program have fabricated a story to make people believe that they are working for a good cause. The win-locker has been named after an emblematic historical character, associated to heroism and justice. While the legends about Robin Hood are a mystery to this day, technology has allowed us to discover the truth about RobinHood ransomware. The authors of the win-locker are fraud artists. They are not helping people in need. The money they collect from computer users go into their own bank accounts.
The cyber criminals claim that they support victims of the war in Yemen. The win-locker drops a file titled READ_IT.txt. It contains a stern message, talking about Bin Salman of Saudi Arabia. This is a real person who is associated to the events currently taking place in Yemen. The message states that everyone who takes no action against this regime is a Saudian or Supporter of their activities. This is stated as the reason for the ransomware attack.
The ransom note gives users three options. You can pay a sum of 5 Bitcoins which would be sent to help Yemeni people. This amounts to about $21,183 USD. The other option is to post a statement on Twitter. You have to condemn Bin Salman for his crimes and ask him to end the war. The post you make needs to get at least 100 retweets. If you do not take either of these actions, you will lose your data. This would mean that you support the regime in the war against Yemen. The scammers behind RobinHood ransomware try to affect people emotionally by making them feel guilty.
If you choose the option to pay the ransom, you have to be quick about it. The transaction has to be made within 72 hours. The remaining time is shown by a program titled ROBINHOOD -TIMER.exe. This utility displays an animated wallpaper. It depicts the harsh conditions in Yemen by showing a selection of images. A count down clock will keep you updated on the time you have to contribute by making a payment. Copies of both the ransom note and the timer are placed into every folder which contains encrypted files. RobinHood ransomware targets different objects. This includes documents, images, archives, databases, videos, audios, logs, and others. It appends the .Robinhood extension to the names of the targeted files upon encryption.
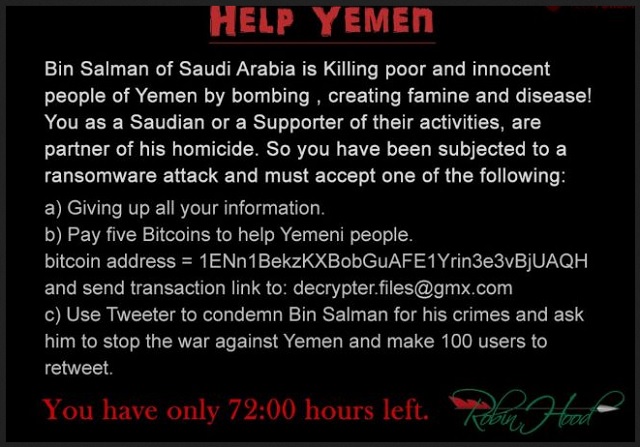
The supposed financial aid is to be provided in Bitcoins. The Bitcoin wallet address is listed in the ransom note. When you complete the payment, you have to send the transaction link to the following email address: decrypter.files@gmx.com. There is a reason why the cyber thieves have decided to accept the money in a cryptocurrency. This way, they are able to protect their identity. Bitcoin trading platforms allow users to conduct financial transactions anonymously. The people behind RobinHood ransomware will transfer the received sum to a bank account. It will be impossible to identify them.
Our advice is not to pay the cyber crooks. Even if your only concern is getting back your files, you should still reconsider. There is no guarantee that the owners of RobinHood ransomware will make good on their end of the deal. They may not decrypt your files. It would be for the best to attempt to recover your data on your own. This can be done by using shadow volume copies. There are several tools which can assist you in the process. We have listed them below. They are all free.
To protect your computer from viruses like RobinHood ransomware, you need to be on the lookout. The win-locker is spread through spam emails. The sender behind the letter will try to convince you that it is a genuine notification from a legitimate entity. He can write on behalf of the postal office, a courier firm, a bank, a government branch, an institution, a social network, or the police department. The payload of RobinHood ransomware will be packed with an attached file. Before following any instructions from an email, you need to proof the listed contacts. Be advised that opening an infected file is enough to transfer a virus to your computer.
RobinHood Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, RobinHood Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since RobinHood Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

