I wrote this article to help you remove Ramsey Ransomware. This Ramsey Ransomware removal guide works for all Windows versions.
Ramsey ransomware is a win-locker which resembles another encryption virus. The creators of this program have copied Jigsaw ransomware, a notorious infection which has been roaming the cyber space for over a year. Ramsey ransomware uses the same design for its notification window. Rather than producing a ransom note, the nefarious program opens a dialog box. The message is written in Turkish, as the virus targets users from Turkey. If you are unfamiliar with the concept of this kind of infection, we can explain. Ramsey ransomware encrypts files. This process renders the objects’ code schemes which makes them unreadable. You will be unable to access your rightfully owned data. To decrypt their files, the developers of the win-locker demand victims to pay a certain sum. This fee is referred to as a ransom, hence why the other name for this type of virus is ransomware.
Ramsey ransomware targets different file formats. This encompasses text documents, spreadsheets, presentations, images, audios, videos, archives, logs, compressed folders and others. The infected objects are marked with the .ram suffix. As the ransom message discloses, the encryption scheme consists of two layers. The authors of Ramsey ransomware have chosen to make a combination of a 2048-bit and a 256-bit RSA cipher. A lot of win-lockers deploy the RSA algorithm. This asymmetric cryptographic technology creates a sophisticated code scheme. The process can be reversed with a decryption key. This is what the ransom is paid for. The renegade developers have set the insidious program to generate a unique set of encryption and decryption keys for each target machine.
The proprietors of Ramsey ransomware demand victims to pay a ransom of $25 USD. This amount converts to $87.27 TRY, according to the current exchange rate. The hackers require the sum to be transferred in Bitcoins. This is a cryptocurrency which provides optimal security. When opening an account on a Bitcoin platform, users are not required to disclose personal information. Withdrawing funds is just as secure. The ransom is to be transferred to a digital wallet. It is listed in the ransom message. Upon receiving a payment, the thieves can safely withdraw it to a bank account. Bitcoins trading platforms cannot track the route of a transaction.
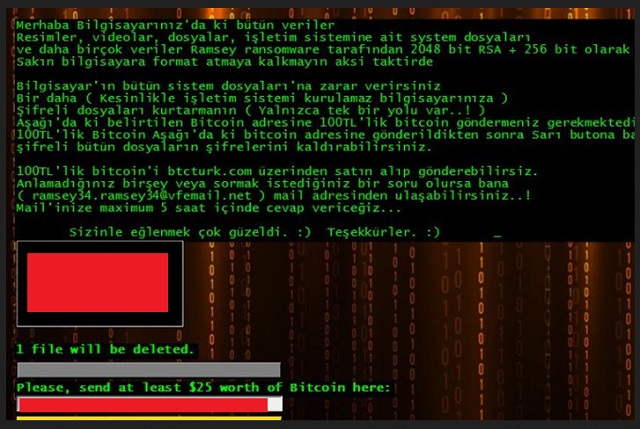
Like the program it is based on, Ramsey ransomware has an additional function which allows it to pressure its victims. The clandestine program can delete the infected files. It begins the deletion 24 hours upon completing the encryption. The win-locker is set to delete 1 file every hour. It chooses which object to erase next at random. This pattern is scheduled to continue for 3 days. Victims are given 72 hours to transfer the ransom. If they fail to do so, all remaining files will be permanently deleted. This is a sound strategy, as it gives victims limited time to act.
Our advice to users who have contacted Ramsey ransomware is not to meet the demands set forth. Keep in mind that the people behind the win-locker are cyber criminals. You should not trust fraud artists under any circumstances. Making a deal with them would be a risky endeavor. They may not fulfill their part of the agreement. It is not uncommon for hackers to collect the ransom money and break contact with the victim without sending the decryption key. Even if they provide it, they may launch a second attack in time. You should look for an alternative solution to the problem.
Resolving the issue will be a challenging task. The developers of Ramsey ransomware have taken measures to prevent users from recovering their files. The win-locker deletes the Shadow Volume copies of the locked objects. These remnants can function as a backup. They contain the data of the files you have saved to your hard drive. Furthermore, the malignant program will render the actual inaccessible. Ramsey ransomware can tamper with certain system components. The most relevant intervention is disabling the System Restore feature which makes the backups impossible to use.
Ramsey ransomware is distributed via spam emails. The secluded program travels hidden behind an attachment. The sender will present the file as an important document. He can write on behalf of an existing organization, like the national post, the district police department, a courier firm, a bank, an institution, a government branch, a social network or an online shop. To make the email resemble a genuine message from the corresponding entity, he can add its logo and contacts in the body of the letter. To check whether your incoming postage is legitimate, look up the address it was sent from. While spammers can copy the publicly available information on a given organization, they cannot access its official email accounts.
Ramsey Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, Ramsey Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Ramsey Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

