‘Today we have launched the Petya Ransomwear Project’; this is a proud statement from the page that greets a visitor to the TOR website after being infected with this new trojan-ransomware. Unlike other ransom malware that is in circulation at present, Petya does not limit itself to encrypting user files – it essentially locks up the Master Boot Record (MBR) by encryption so that an entire operating system cannot function at all. It achieves this by overwriting the MBR and causing Windows to crash. If the PC is then rebooted, a skull-and-crossbones motif will is displayed followed by a demand of 0.99 Bitcoins (approx. $430 U.S) to free the system; this price doubles after seven days. It is thought by some analysts that Petya could be an updated version of another similar though less evolved infection that was briefly seen at the beginning of the year.
Infiltration
The ransomware’s delivery method is by e-mail which has an attachment and is aimed at Human Resource staff disguised as a C.V (or Résumé) . They are personally addressed to the H.R staff of a company and not merely generic spam. This follows an increasing trend of ransomware targeting commercial networks. So far, Petya’s developers are primarily targeting German businesses, though similar e-mails have started to be reported in the Benelux region. The C.V is really a self-extracting executable file provided by a legitimate cloud storage (Dropbox) link. The link’s title is ‘Bewerbungsmappe-gepackt.exe’ which translates as: packaged application portfolio. There is also a ‘photo of the supposed applicant included to add verisimilitude to the masquerade (this is a commercial ‘stock’ picture and obviously used without permission). When the link is clicked, the trojan is downloaded and executed. Several factors with this malware support the increasingly commercial targeting trend and the growing sense of professionalism/commercialism in the ransomware industry:
- The delivery method is staged to be very formal and believably like a legitimate corporate application;
- Legitimate commercial cloud storage is used for delivery (N.B: when Dropbox were notified they quickly removed the file);
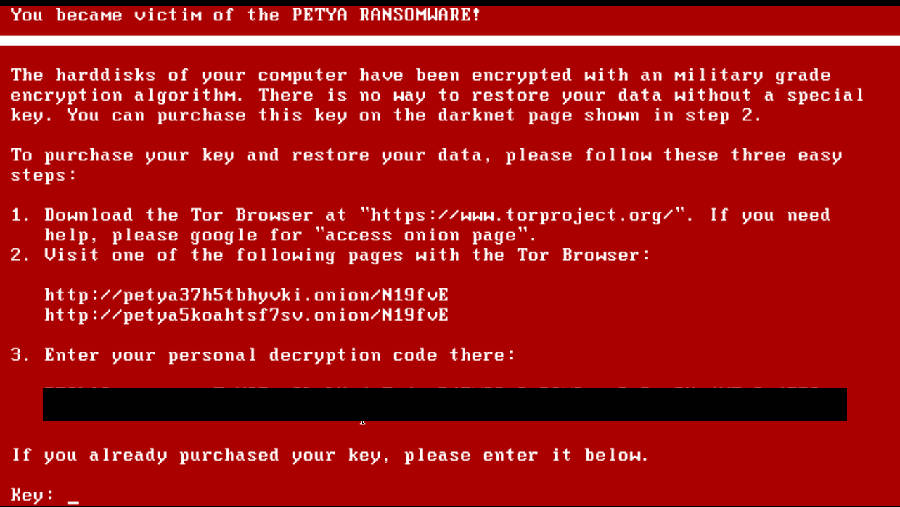
The formality and formatting of the TOR ‘site layout is like a typical corporate service ‘site, even including translation, links for customer support and FAQs; - As there is no way to access the internet from the infected system, the victim must use another clean machine to access the TOR ‘site. This will not be a problem in a work environment. This lack of access is the antithesis of other customer-friendly ransomware that is configured to make the payment process as easy for a private user as possible.
The name Petya is a diminutive or familiar version of Pyotr. One the most famous examples of this name is Count Pyotr ‘Petya’ Ilyich Rostov of Tolstoy’s classic novel War and Peace. The character is fatally wounded whilst battling the French invasion forces in 1918. Another notable Russian Peter was the Tsar of the same name who is remembered in part for his aggressive foreign policies. The name is particular to Russia – and the Slavic states that are – or were – under Soviet dominion. The Hammer and Sickle insignia on the developer’s website seems to bear out the fact that a former Soviet Union country is the likely origin of the ransomware, though this cannot be taken for granted, especially given the depths of deception and obfuscation that malware authors got to in order to hide their identities – and sometimes their products – from scrutiny. It is interesting that the Petya Ransomware corporate logo spells ‘Ransomware’ with a combination of both Cyrillic and Latin characters; also, that the e-mail text is written in excellent German and is not a mechanical and flawed web-based translation like some second-language ransomware texts are. Sometimes, a mistake due to the vanity of mal-authors can provide a clue to an infection’s origins, though at the time of writing Petya’s nationality remains unknown.
Encryption
When the Petya malware first appeared there was a difference of opinion as to whether it was truly cryptoware (that it did indeed encrypt the hard drive), or that no encryption took place and that the ransomware used more traditional lock-ransomware tactics which block a user from their data until payment, and many times is circumventable. Some online I.T commentators made the error of underestimating Petya’s operation and confidently proclaimed that files were merely locked and not encrypted: ‘…only the file access is blocked but the files itself are not encrypted.’ [Petya; G Data; 28/03/16] .
This company did express that it was only their assumption at the time of writing. There are other ‘sites that have taken this assumption on-board as certainty and have gone as far as to offer a quick fix by using the FixMBR command to repair the Boot Registry, remove the infection and recover files. By attempting this the screen-lock will be removed, but with the Master File Table still encrypted, both Windows and user files will still be inaccessible. If there is an external file back-up or there is no need to recover files – and the user is prepared to reinstall Windows – then this method is an option.
Analysis is still ongoing at the time of writing, though the consensus it is now held that encryption does take place. The Petya infection’s instructions inform of encryption by a ‘military grade encryption algorithm’, though many malware statements in the past regarding the encryption that is employed has been false or flawed, either for obfuscation or for customer effect; many variants claim to use RSA 4096 with a link to take the victim to Wikipedia to read just how highly encrypted their files have become. It was later discovered that often the code was either the lower 2048, or AES 256. This is practically irrelevant because without a coding flaw to exploit or a key, decryption is not possible for a home-user, and not viable for commercial enterprises, even if the lower algorithms are used by the malware.
What must be remembered when discussing Petya or any other malware – it is allowed entry to a system directly – or indirectly – only by human error.

