Linux running web servers appear to be at risk of a new strain of ransomware called FairWare. Three Linux administrators, at least for now, have already complained about being targeted by the malicious newcomer.
People, who were having trouble with ransomware support thread and posted their quandary on the Bleeping Computer forum and the Chinese V2EX Q&A site, alarmed they have been hacked. The said the attackers had removed their website root folders and had left a short ransom note in the /root folder.
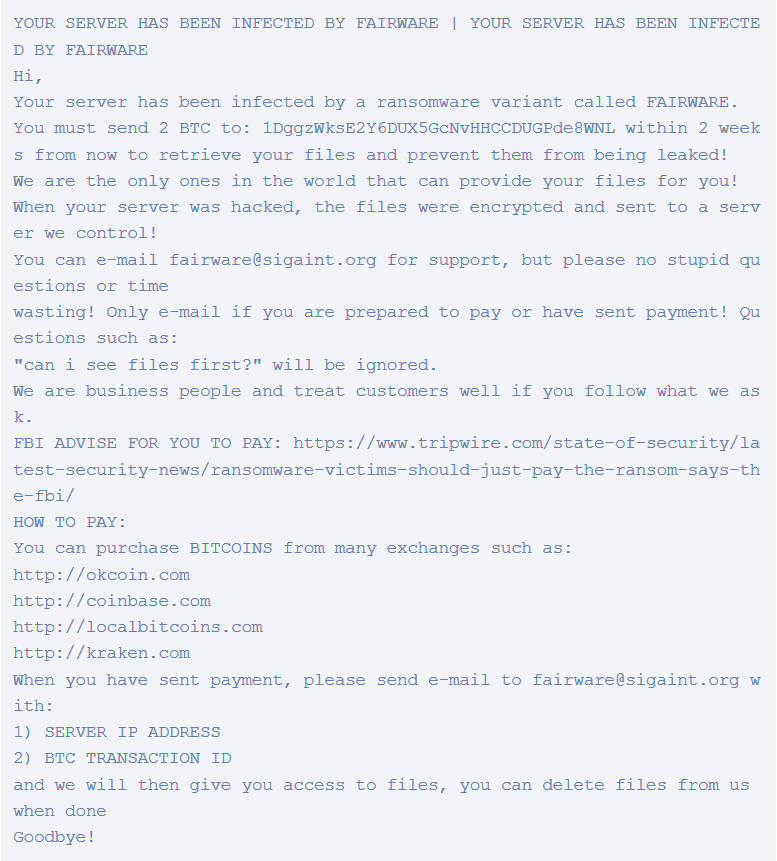
This ransom note, named READ_ME.txt, stated only the following:
“Hi, please view here: http://pastebin.com/raw/jtSjmJzS for information on how to obtain your files!”
Visiting the link victims see a more detailed ransom note with a message from the crooks, payments instructions and an email address for the victim to get in touch with the hackers. The note also includes a ransom sum, 2 Bitcoin ($1,150), which the victims should pay in the Bitcoin wallet.
Security expert and a founder of Bleeping Computer, Lawrence Abrams, states that, for the moment, it is not clear if the FairWare actually encrypts victims` data. He supposes that the hackers may be just bluffing and uploading the files to their server and keeping them hostage until the payment is complete.
Abrams also thinks that there is a high chance the crooks may be deleting the files for good and even if a victim decides to pay, they might get double-crossed. In the longer ransom note, FairWare devs warn they will ignore any user asking them to prove that they still have the files.
Despite the hackers` warning, users are advised to try getting a proof that they data is still intact before completing the ransom payment.
For the moment, there are no payments in the Bitcoin wallet address shown in the extended ransom note, which you can see below.