VirLocker ransomware came back with a vengeance last week after a lengthy absence. The virus was first spotted in 2014. It is part of a ransomware family first dubbed Operation Global III. Later on, the group of infections went through name changes, including VirLock, VirRansom, and VirLocker at present.
The ransomware was passive throughout its tenure up until now. VirLocker was not part of aggressive distribution campaigns, characteristic for the top-tiers in the branch. New versions continued to surface, including a notable update in January of 2016.
The new variant of VirLocker can be cracked without a decrypter
A year later, computer users are faced with the next chapter in the ransomware’s history. To start with the good news, the latest reincarnation has a major flaw. The new version of VirLocker can be cracked. Victims do not need to pay a ransom to have their files recovered.
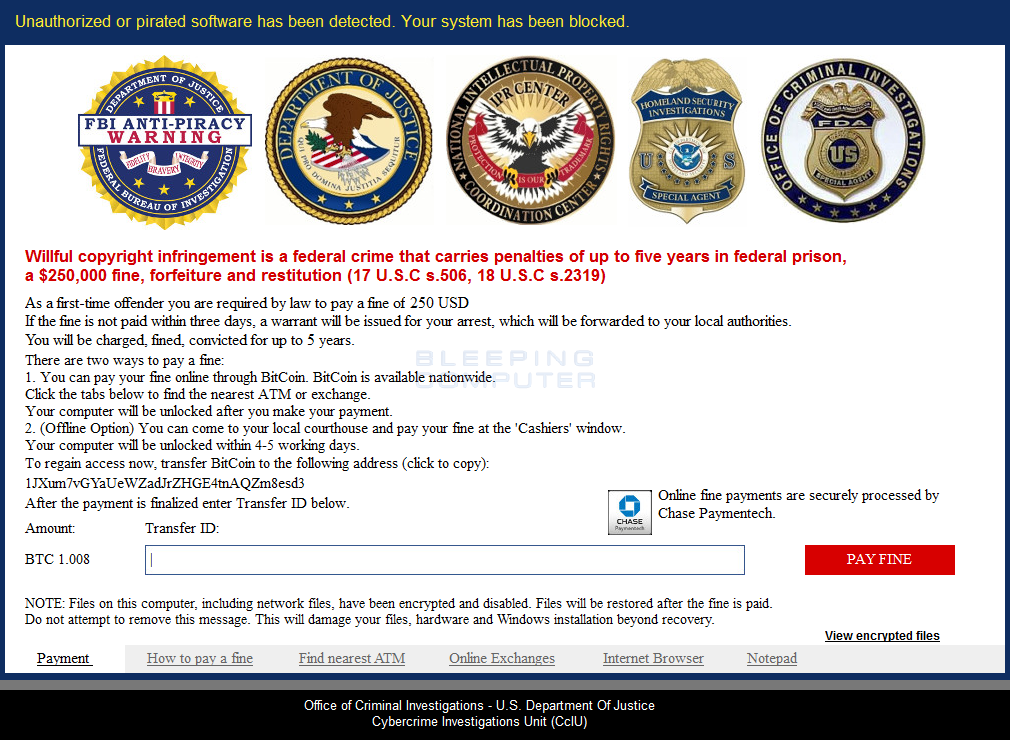
The ransom note of the virus has a field for entering the decryption key. It is situated beneath the “Transfer ID” sign. You can make the program believe you have paid the ransom by entering 64 zeroes in the field.
VirLocker displays a sophisticated approach to encrypting files
All versions of the ransomware since its inception have used a complicated encryption pattern. VirLocker wraps each targeted item in an .exe package. This operation consists of two processes. The virus first encrypts the file and then it packs it in an executable.
Since the original file name is kept, the infected objects may look deceptive. Most Windows versions hide the last file extension, so you may not realize that the actual format is .exe.
The most concerning aspect about VirLocker is that it places a copy of itself inside the executables. This means that all encrypted items are a potential host of the ransomware. You can spread the virus to another device by transferring an infected file. Moreover, the program will still be present in your system after doing an independent decryption.
Performing a decryption does not deactivate VirLocker
The flaw in the code of VirLocker does not make it possible to delete. Using the 64-zero code would allow you to access your files. You will need to manually go through each executable, extract the containing file from it, and delete the binary. Remember, every malicious executable contains the payload of the virus.
To recover a file, you need to double-click its .exe. Doing so will extract the original file from the binary. After you have recovered a file, you need to delete the executable where the encrypted version was contained.
Format your hard drive and reinstall Windows to prevent another attack
While in theory it is possible to restore all your files and delete all copies of VirLocker, this would be a risky endeavor. The ransomware encrypts files in different folders and directories. Since all infected objects are a host for the virus, omitting a single executable can lead to the infection being reactivated.
The best course of action is to recover your important files, store them on a separate device, and erase all data from your hard drive. You should reinstall your operating system altogether. This is the only way to delete all copies of VirLocker.