I wrote this article to help you remove LambdaLocker Ransomware. This LambdaLocker Ransomware removal guide works for all Windows versions.
LambdaLocker ransomware appeared on the malware scene recently. This win-locker uses a combination of the AES-256 and the SHA-256 algorithms to encrypt various types of files. These include documents, pictures, PowerPoint presentations, archives videos and others. The ransomware adds the .lambda_l0cked suffix to the name of each encrypted file. For example, example.exe will be renamed to example.exe.lambda_l0cked. The virus will notify the user about its existence with a ransom note in the form of an HTML file named “READ_IT.hTml” which will be saved on the victim’s desktop.
LambdaLocker ransomware gives the user only one month to pay the ransom. After the time is over, the personal decryption key will be permanently deleted. Don’t fall for this. It is a psychological trick used to push the victim into impulsive actions. You have enough time to find information about the parasite and gather opinions about it. Keep reading for more information about LambdaLocker ransomware and make an informed choice.
LambdaLocker ransomware drops a ransom note written in both English and Chinese. It states that the victim must make a payment and then write to the lambdasquad.hl@yandex.com email address to confirm that the transaction has been completed. Judging by the account, we can speculate that this virus is a Russian or a Ukrainian one, created to target computers in China. Of course, those are just speculations and users all around the world may get infected with that dangerous parasite. This statement is supported by the fact that six out of the ten Bitcoin platforms the virus recommends are Chinese.
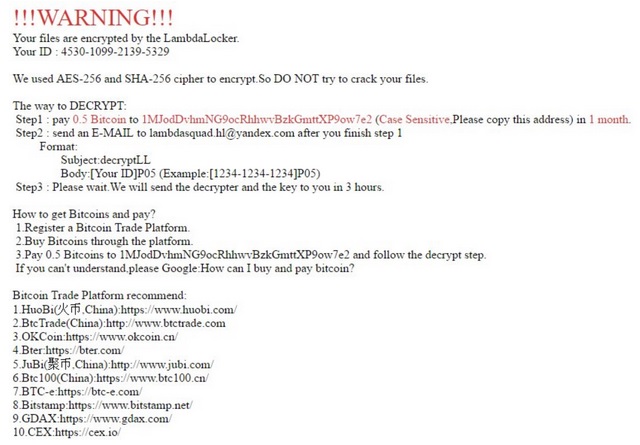
LambdaLocker ransomware demands 0.5 Bitcoins (approximately 625 USD) as a ransom in exchange for a decrypter and a personal key. For the reasons listed below, we do not recommend paying the ransom. First of all, you can never win a game with hackers. Second, the ransom note states that the victim must contact the hackers to confirm that the payment has been made. But, how can you be sure that the crooks will contact you back? Even if they do, they may send you a key that is not working properly or they may ask you for more money. There are such cases, so don’t rush.
LambdaLocker ransomware gives each victim a personal ID. This ID should be mentioned when the user contacts the crooks. They guarantee that if the victim follows the instructions strictly, they will send a decryption key within 3 hours after they receive the email. This sounds very promising, but nothing more. The Bitcoin currency is impossible to track down. If, for example, the hackers forget to contact the victim, no one will be able to help them, even authorities. Keep this in mind before proceeding to pay the ransom.
However, if you choose to pay the attackers, we must warn you that the decrypter will only restore your files. It will not remove the LambdaLocker virus. It is possible for the parasite to re-encrypt your files anew. How many times are you willing to pay for your files? Besides, perhaps there is a way to restore them without the decrypter. If you have a system backup, you can use it to restore your files. Don’t forget to remove the infection before using the backup. Otherwise, your newly restored files will be encrypted, too.
There are many ransomware distribution techniques. Spam emails are commonly used for spreading ransomware. The hackers tend to design their letters to resemble official notices from legitimate institutions. Those people won’t hesitate to steal official logos and fabricate stamps in order to trick you into downloading an attached file. Remember that the authorities will use an official method to contact you. Certainly not through an email. When you receive a letter from an unknown sender, don’t download anything before proofing their credentials. For example, if you receive a letter from an organization, visit their official website. There, under the contact section, you can find their official email address. Compare it with the one you have received a letter from. If they don’t match, delete the message immediately.
LambdaLocker Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, LambdaLocker Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since LambdaLocker Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

