I wrote this article to help you remove Explorer Ransomware. This Explorer Ransomware removal guide works for all Windows versions.
Explorer ransomware is a win-locker. Its purpose is to make users pay a certain sum. The malicious program achieves this by encrypting their personal files, thus denying them the right to access their own data. By analyzing the code scheme of Explorer ransomware, malware experts have discovered that the encryption is performed with the use of AES cryptography. This is a symmetric encryption algorithm. The win-locker adds the .explorer appendix to the names of the encrypted files. To notify users of its actions and announce its demands, Explorer ransomware leaves a ransom note. A copy of the file is placed into every folder which contains encrypted objects. In addition, the covert program changes the desktop background to a custom wallpaper. The contents of the document are written on the graphic in a larger font.
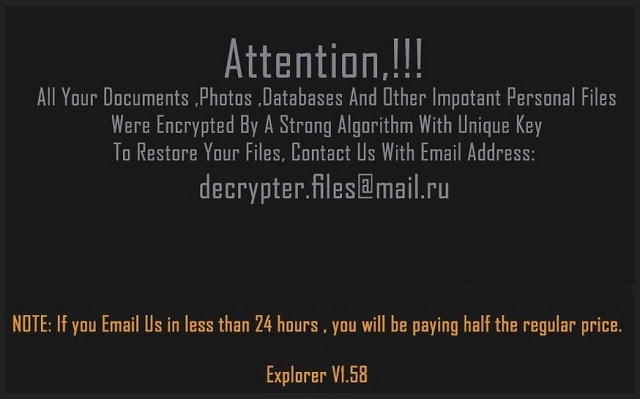
The ransom note is titled READ_IT.txt. It makes a clear and concise statement about the situation at hand. As explained, Explorer ransomware has encrypted all your documents, photos, databases, and other important personal files with a strong algorithm with a unique key. To have their files restored, victims are instructed to contact the cyber criminals. You will have to send a request to their email address: decrypter.files@mail.ru. Upon contacting them, you will receive word on the amount of the ransom and instructions on how to pay it. The renegade developers have a tactical approach on the matter. They give people the chance to pay half the price. A reduction is made for users who contact them within 24 hours.
Since the owners of Explorer ransomware do not provide complete information until after the victim has contacted them, there are some holes to fill. For instance, the amount of the ransom is yet to be revealed. The details on the payment process are not completely familiar, either, but we do know the method. Like most win-lockers, Explorer ransomware requires victims to pay in Bitcoins. This is a cryptocurrency. It is chosen as the means of payment because it protects the identity of the recipient. The owners of the win-locker can collect the ransom without taking a risk. Upon receiving the sum, they will transfer it to a bank account. The transferal will be protected. It is impossible to follow the path of the funds to the account of the hackers.
Contracting a virus like Explorer ransomware is stressful. The attackers will do their best to further pressure you. This only makes sense, as the goal is to get you to pay the ransom. It is not advised to meet the demands of the cyber criminals. The financial settlement they require users to make is not official. There is nothing to stop them from collecting the sum and leaving your files encrypted. For this reason, our advice to users is to take the initiative in their own hands. You can recover the data from the encrypted files by extracting it from their shadow volume copies. The Windows operating system is set to store them per default. We have listed a few tools which can help you in the process.
The best way to combat against computer infections is by maintaining a high level of security. Up to this point, all versions of Explorer ransomware have been spread in the same manner. The secluded program travels with spam emails. The sender will compose the message to seem genuine. He will direct your attention to an attached file, stating that it is an important document. This is the physical host for the win-locker. With the help of a script, a macro, or another component, the transfer of the clandestine program will be automatized. Be advised that accessing the containing file is enough to have the virus transferred to your machine. You should do your research to confirm the reliability of your in-box items. Check the email address and other listed contacts. Keep in mind that spammers often write on behalf of legitimate organizations, like the national post, the local police department, courier firms, banks, institutions, government branches, social networks, and shopping platforms.
Explorer Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, Explorer Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Explorer Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

