This article provides a free solution on how to decrypt Locky ransomware. Follow the steps in this guide to restore .locky files
This is trojan-ransomware: an infection is delivered by a trojan that then communicates with its C&C server (command and control) to download the ransomware. It is important to detect Locky at this stage, if it enters. Once inside the operating system the ransomware executes, changing certain Windows files and drivers, then it starts to encrypt user files. The key – un-cracked at present – is only available from the hackers in return for a ransom payment (currently 0.5 – 1 Bitcoin or $400 US). Another task the ransomware undertakes is to try to delete VSS files (shadow copies) preventing file retrieval from system backups. It has been described as ‘well designed’ malware and incorporates some relatively new features: it locates and encrypts Bitcoin wallets if the user has one, making the ransom even more important for some people. It also encrypts network shares leading possibly to major disruption for unprepared businesses (see prevent section below). This is thought to be only the second ransomware (along with DMA Locker) to use this feature and backs up the evidence that hackers are increasingly targeting commercial networks for greater profit.
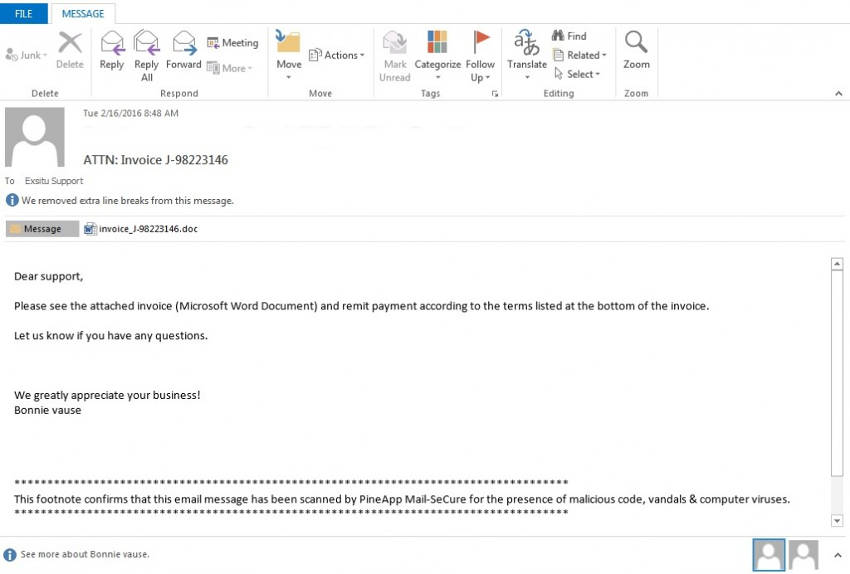
Last year, a shift was seen to start in the infection numbers of small-to-medium-sized businesses that, in some ransomware, accounted for almost 50% of victims. This is one example of an increasingly progressive strain of ransomware variants that can cause a great deal of trouble – users should take all precautions to stop Locky entering a system or network as dealing with the infection is much more difficult than its prevention. If a recent (external) file backup has not been made, carry out this task as soon as you’ve read this article.
The Locky ransomware was launched in February this year, and initially thought to have targeted 400 000 computers. This was assessed as a trial run as infections have increased dramatically in the last week. Researcher Kevin Beaumont estimates that between one to five computers are being infected every second, making this what has been described as a ‘major cybersecurity incident’. These figures come from monitoring traffic around some of the C&C servers that the hackers are using to deploy the ransomware. It hasn’t been possible to take down these servers at present because of the complex and evasive way the system is designed to run.

Trojan-ransomware is delivered by several routes. It can come as part of a bundle of freeware that is downloaded and installed without the user looking at the contents beforehand. There is a risk from infected links such as fake pop-up ads for freeware updates. Exploitation kits can target vulnerabilities in a system or its apps whilst browsing on compromised/dubious ‘sites. Manual hacks can be employed targeting undefended network or remote access points. Using external devices that are unwittingly infected can introduce the malware. And there is the spam ‘mail method which is employed in the delivery of the Locky ransomware. This involves a piece of ‘mail that is carefully crafted to appeal to the user to open it (cases of language/geographical/commercial tailoring to certain targeted groups of users have been observed). A seemingly legitimate or official document will have an incentive for the victim to a link or attachment that will install the trojan if clicked on. In some e-mails, the text may look like unreadable code, and you will be requested to enable macros to read it in plain text – doing this will install the trojan.

As this bug has network encryption capabilities (capable of encoding shared files over large networks), it only requires one fake e-mail to slip into a weak system and be executed for data chaos to ensue. It is vital – and perfectly possible – to block Locky and other ransomware infections.
Detecting and dealing with Locky ransomware
Ransomware is designed to evade all but the most stringent or specific scans and different specimens vary in this ability. Many security suites will not detect an infection from a new variant until it has been recognized and its signature is programmed into the software’s data-base for reference. It is important if infected to identify and terminate Locky as soon as possible – this can minimize data loss and make recovery more successful if its deletion of backup files is halted. There are manual signs that users can be on the lookout for that may indicate the presence of malware: unprompted internet connections being made and unusually increased levels of activity at ports; higher CPU usage than normal – so slower than normal operating speeds; freezing of display momentarily and programs crashing. If these signs are noticed, then all network and internet connections – wired or wireless – should be disconnected. If no external file backup is available, make one immediately though ensure that all files have their original extensions. If there are any changed or questionable extensions, place in a separate folder. Check any networked links for infection. See below for instructions to eradicate Locky. If files need recovering, first try Previous Versions, or if this doesn’t work use the Shadow Explorer software (see windows.microsoft.com for details).

How to decrypt Locky ransomware and restore encrypted .locky files?
Unfortunately, there is no standalone Locky decrypter at this moment. The good news is that leading security researchers are working on making such decrypter. Until a Locky decrypter is done, you may try these steps to decover .locky files:
Method 1: Restore your .locky files using ShadowExplorer
Usually, Locky ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your .locky files, encrypted by Locky ransomware, using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Locky ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:
Method 3: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
How to prevent Locky ransomware
Remember that preventing Locky and extortion-ware like it is simply a matter of user discipline and an awareness of how malware can be contracted. The first consideration for stopping infections is to maintain an up-to-date system. This includes operating system security patches and ensuring that you’re using the latest version of your browser; place browser settings to their highest that still allow access required and warn of hazardous ‘site content. Disallow all add-ons, plugins and extensions. Install a good firewall that will cover ALL routes – including remote and networking connections; set this to disallow communication on Tor and I2P networks (so that if a trojan does gain entry, it cannot communicate and execute), block unauthorized port use. Get the best security software possible that will carry out in-depth scans. For good measure, make backups as regularly as possible to external storage.
The next consideration is settings, or privilege. On a network of any size – family or business – do not use the Administrator log-in for general use, or stay logged-in for longer than necessary in this capacity. It’s safer to give the username/password to everyone who may need it with the instructions to log-off when a task is completed. Allow strictest Admin privileges that still enable the network to function (see the Microsoft website for more detail on this).
The easiest element of prevention is good working practice – though perhaps this is sometimes the most difficult to enforce or adhere to. Bear in mind the delivery routes mentioned above. In the case of the e-mail delivery threat, depending on a system, set ‘mail to highest security. Ensure that all users are aware of the risks of opening unsolicited ‘mail. Disallow ActiveX (macro) function for all Microsoft Office applications. Find a method to filter incoming containing attachments and preview if neccessary by left-clicking and viewing Source in Properties which will supply the body of the text and display any hidden attachments without actually opening the file (DO NOT preview in Print Preview, as this can execute some malware).
Stay organized and up-to-date – don’t let this current threat know your business!


I don’t get it, why go through this whole process when you can just install an Anti-Malware like MalwareFox and let it do the work for you? It saves a ton of time and energy.