If you are looking for a free way to decrypt CryptInfinite encrypted files, this article is just for you. Follow the steps below to successfully decrypt CryptInfinite files.
This is a trojan-ransomware infection that emerged in November 2015. Although a key has been developed (see link), the user should delete CryptInfinite if detected as it can offer a possible back-door for other malware without solutions or be used to steal data. The trojan element gets itself installed by deception (see below) and then the malware creates an inconspicuous file named as XBMGERoOjZX.exe to operate from in the %AppData% folder. On the next system start, it runs and works to change certain Windows files and registry then makes a call to its command server from which the ransom element is downloaded and installed. The ransomware then generates a unique ID for the user and creates a executable file with this name (XXXXX.exe, for example) in %UserProfile%. Then an attempt is made to delete Shadow Volume and disable Start-Up Repair – though the user must click a User Account Control (UAC) prompt that will be presented to enable this. This process is to wipe file copies that the user could later re-install. Certain system applications that may indicate infection are also terminated. The ransomware will then go about encryption giving all files the extension .crinf and when finished will display a .txt file outlining how to pay for the key (currently $500 U.S via PayPal, payable within 24 hours). For decryption using the Emsi software, the e-mail address given in this ransom note is needed.
At the present time, this malware is being distributed using spam e-mail that comes in the form of a fake résumé (or C.V) purporting to be from an individual looking for work. This fits with the growing consensus that hackers are increasingly targeting business and commercial networks though this particular ransomware does not yet have network share capabilities. During the last year it has been noted that small and medium sized businesses have accounted for nearly fifty percent of successful infections (despite these networks having an even greater vested financial interest in maintaining security than the private user). These spam runs were made to target office hours and were adjusted in different locations to account for the differing time-zones. From a commercial point of view, it is important to avoid CryptInfinite because although there is a key for this variant villain, if this one could enter a network then a much more proficient and uncrackable piece of ransomware could gain entry by exactly the same route.

A user must open the spam ‘mail and either open an attachment or activate a macro in order to initiate the download of the trojan. The résumé was supposed to be in response a job advertised on Craig’s List. Obviously, many people in offices receiving this spam will not be in the H.R department of a company, and may not even be in a sector that is open to recruitment, though this is another element of the increasingly complex social engineering that is coming into play in the wide world of malware distribution. In this instance, although the recipient is very unlikely to be able to offer the sender a job, there is a good chance that a member of staff with inadequate I.T training WILL open the letter (and the attachment/macro): to either be helpful and redirect the job-seeker in the right direction; to simply inform him/her that they have the wrong address; out of curiosity to read this person’s history while things in the office are quiet… and before you can say ‘Trojan-Ransomware!’ – the malware is there and the employee has compromised the company. Other social-engineered ‘mail can be more personal and even make some kind of reference to the recipient by using simply hacked data like geo-location. They can also be intimidating and authentic-looking documents apparently from a government office or law enforcement agency that demand attention.
There are other routes a trojan can take to enter such as in unexamined freeware/pay-per-install bundles hastily installed; via fake pop-ups for freeware updates and anti-virus scans; they can be dropped by exploitation kits during a visit to a compromised ‘site; acquired through torrent/file-sharing on P2P networks; through old-fashioned manual hacks into an unsecured network or remote protocol connection, and by accidental contamination caused by using infected external devices. It should now be clear to see that malware infestations ARE preventable, and that to stop CryptInfinite entering the system is less trouble than dealing with it once inside.
Detecting and removing CryptInfinite
As there is a key for decryption available, the first step is to confirm that if infected, it is indeed the CryptInfinite malware. Although many anti-malware programs may not detect the infection initially, there are signs that may be visible to the user, depending on variables like the CPU and memory capacity of the system. The first sign to watch for is the UAC prompt appearing. If this has been authorized by the user (!!!), then programs may start running at slower speeds, indicating the malware running in the background and this may be accompanied by erratic behavior like screen-freezes or early termination of programs due to decreased processing power available. Check for the above malware files and for any changed (.crinf) extensions in user files. In folders that have been fully encrypted there will be a ransom note; make a copy of this for decryption reference. Disconnect from the internet and all other connections and make a backup to an external device of all unaffected files. If external backup files are available, try a system restore (this may need to be re-enabled) to a point before infection, and when you are confident that everything is clear, re-instal files. If a backup is unavailable to replace encrypted data, follow the instructions below to completely eradicate CryptInfinite, then download the software to decrypt any corrupted files. After this is done, have a coffee and think about how this extortion-ware got into the system, and how to tighten things up.
How to decrypt CryptInfinite encrypted files
To successfully decrypt CryptInfinite files, please follow the steps below. Try to perform the actions as strictly as possible. You need one pair of encrypted and original file, in order to generate a decryption key.
Step 1: Download the free CryptInfinite decrypter from there: http://emsi.at/DecryptCryptInfinite
Step 2: Drag-and-drop an encrypted file and his original at the decrypt_cryptinfinite.exe file.
Important!!! You must select both the encrypted and unencrypted version of a file and drag them both onto the decrypt_cryptinfinite.exe executable!
Step 3: Next, a User Account Control window will appear. Click OK.
Step 4: On the next screen, you will have 2 options for the e-mail of the ransom note. Please select either 1 or 2 (the one that contains the associated email addresses for your encryption).
Step 5: The program will start the bruteforce process for determining the decryption key. This may take long, so please, be patient.

Step 6: When the bruteforce process is done and the decryption key is found, you will see a screen like this below:
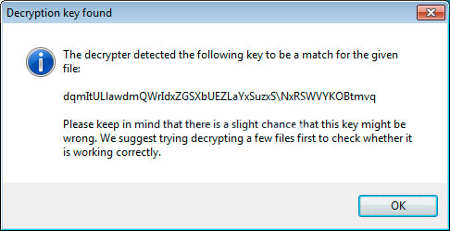
Step 7: Click the OK button at the window. The real decryption process will start. When you see a License agreement, please click Yes.

Step 8: Click Add Folder to add a folder with encrypted files. Add as many folders as you need. When finished with adding folders click Decrypt. All of your files should now be decrypted.
How to prevent CryptInfinite
In this infection so far, the ‘mail route is most common. For business, Administrators should take a close look at policies and privileges and restrictions regarding ‘mail, and the filtering and quarantine options that different set-ups allow. For the home user, it is best to delete anything that comes from unknown addresses or is unprompted. If there are items that may be important to view, first ensure that the ActiveX function for all M/S Office applications is disabled. Left-click on the ‘mail in the inbox and from the drop-down select Properties/View Source. After initial header coding, scroll down and this will reveal any plain text and also show any executable elements and attachments contained. IF there is mostly code with an instruction saying that you must enable ActiveX to view the main text – please DO NOT ever fall for this!! (don’t try to use a browser Print Preview in the same way because this can trigger some malware). A good firewall set to block TOR and I2P networks and allow only authorized port use will disable many infections, even if they manage to enter, as will denying executables to run without authorization by setting tight Software Restriction Policies. A good security scanning program further strengthens a system. Always ensure that browsers are current and set to the highest privacy/’site warning and disallow extensions and plugins. Check regularly for system patches.
With proper system set-up, updated technology and good practice, this and other malware can bang on the door all day, but they won’t get in.

