Cerber ransomware is one of the most recognizable encryption viruses and until today it was impossible to decrypt .cerber files. The infection uses RC4 cipher with a 16-byte key to encrypt files and generate a private key for each of item. It changes the name of each encrypted file to a random combination of 10 capital and lower case letters. Cerber ransomware encrypts the private key using RSA technology. The program has a unique specification which sets it apart from other ransomware infections. The developers of Cerber ransomware have created an audio message which informs victims that their private files have been encrypted. The virus “speaks” with a synthetic female voice.
Security software company Trend Micro has reached a milestone in the battle against ransomware. The company’s engineers have completed the development of a tool which can decrypt compromised files. The success rate may not be 100% for programs like Cerber ransomware which do not synchronize threads. A higher CPU means a lower success rate of the decryption process. By running tests, Trend Micro determined a scale in proportion to the memory usage. At 2 CPUs, about 70% of the encrypted files can be restored. When 4 CPUs are enabled, the success rate drops to under 50%.
The following is a guide on how to use the Cerber ransowmare decrypter software of Trend Micro:
Step 1: Select Cerber ransomware from the list
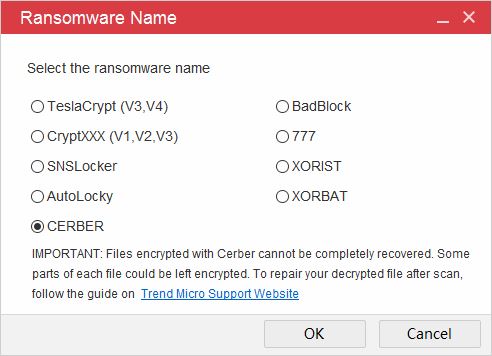
Step 2: Select the items to decrypt

The program can decrypt a single .cerber file or all items from a chosen directory using recursive mode. You have to click on the “Select & Decrypt” button, navigate through your folders and choose the items to decrypt. Then click the OK button to start the decryption process.
Step 3: Conduct the Cerber ransomware decryption

After completing the previous step, the tool will perform the decryption. If you have selected a folder, the process could take longer. The tool will have to collect data from the folder to check which files in it have been encrypted. The user will be updated on the progress through a scrollbar. The total number of encrypted files will be listed and the UI will be updated to indicate the number of decrypted .cerber files.
The duration of the process depends on two factors. The Cerber decryption takes longer because of its nature. The size of the selected files or the content of the selected folder is also relevant.
Step 4: Complete the .cerber files decryption

The UI will display the results of the decryption process once the task is finished. It will inform you how many files were found to be infected and how many of them were successfully decrypted.
The “See encrypted files” option allows the user to view the item(s) he had selected to be decrypted. Clicking on this link opens the source folder.
The decrypted files will be relieved of the custom extension the virus had added to their names. Some ransomware programs (like Cerber) change the entire name of the items they infect. The tool does not restore the original names of the encrypted files.
To return to the main UI, you have to click on the Done button. Then you can proceed to decrypt other items.


Obrigado amigo! Vamos ver se isso resolve!