This page is made to help users infected by Bitcryptor ransomware. Use the guide below to decrypt Bitcryptor files and to restore the original ones
This is a trojan-ransomware infection that covertly enters a system, encrypts files and then demands cash (Bitcoins) in return for the key. This is payable via a command and control (C&C) sever on a ‘Dark’ web domain (the Tor network), where the individual encryption key is also stored. In this case, all the keys are believed to have been recovered so there shouldn’t be a problem for file recovery if infected, though there are other important reasons to delete Bitcryptor if found, and to tighten up security.
The malware has several ways to enter a computer: as attachments or in-text links in convincing, sometimes official looking, spam ‘mail; the quick install of a freeware bundle that contains the malware; by clicking on fake adverts for freeware updates or (rogue)anti-malware offers; on a visit to a dubious ‘site and becoming the target of exploitation kits; by using unverified torrent-sharing; in a traditional hack via unsecured networks, or even by using external devices like flash drives and D.V.D’s that have been accidentally infected. It’s easy to stop Bitcryptor entering if these routes are remembered and covered. The main methods of delivery for Bitcryptor are reported as the spam ‘mail attachments and exploitation kit methods.
The predecessor of this ransomware was the CoinVault infection that was first detected in 2013. In May 2014, researchers linked the infection of at least 1 500 Windows operating systems in over 108 countries to this malware. As a result of a raid in April 2015 by the National High Tech Crime Unit (NHTCU, Holland), a command and control server was seized and an extracted database allowed around 750 decryption keys to be recovered for CoinVault. The authors of this malware went quiet for a while, then launched a new variant that is the Bitcryptor ransomware.
Various security software labs started to work on decryption tools as a result of the release of the previous information by the Dutch Public Prosecution Service. Another raid in September 2015 seized further keys from servers hosted in the Netherlands in an operation that ended in the arrest of two men aged 18 and 22 from Amersfoort, Holland (who both admitted to being the malware programs’ co-authors). One of the labs who have been working with Dutch security and who have created a working decryption tool for CoinVault – Kaspersky Lab – stated that they were sure that the original threat was ‘dead’ and that all the keys (14 031) were seized, and they are confident that the tools developed will now also decrypt this latest version – so eradicating Bitcryptor (a link for the free download is below).
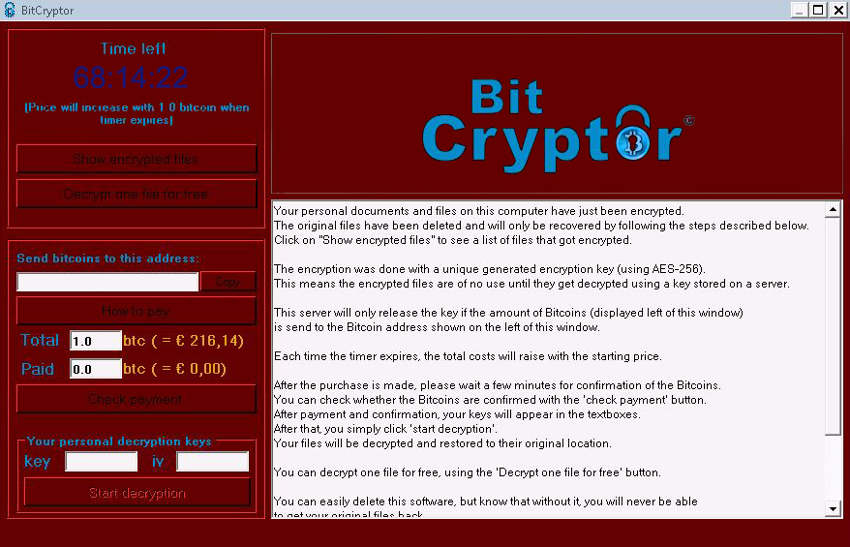
Although the servers have been taken down and the keys are available, there are still reasons to be informed and on guard about this ransomware. Firstly, it may still be extant as an possible infection, lying dormant on contaminated devices or in as yet unopened spam, or in compromised links. So, while no longer effective as a ransom device, it may still require clean-up and file recovery should it be caught (it is unclear whether the encryption process will start to run without any contact with the C&C or not). Though the bigger issue is that if a user has been contaminated by this now neutralized threat, then there is obviously a weakness in the system that could allow other un-cracked and more problematic malware to enter. This second point is why it is vital understand how to defend against Bitcryptor and similar ransomware.
How to decrypt Bitcryptor files
To decrypt Bitcryptor encrypted files, please follow the steps below:
STEP 1: Download the free Bitcryptor decrypter from here: https://noransom.kaspersky.com/static/CoinVaultDecryptor.zip
STEP 2: Extract the .zip archive
STEP 3. Double-click on CoinVaultDecryptor.exe
STEP 4. Click Change parameters

STEP 5. Uncheck List of encrypted files. Check Folder with encrypted files.

STEP 6. Click Start scan. Wait until the utility finishes the decryption process. Sometimes it may take even days, so please, be patient. Do not turn off the computer, nor close the running tool.
Detecting and dealing with Bitcryptor
This variant has evasive tactics to avoid detection by many routine scans from most software, so it is necessary to know the signs to watch for. Bitcryptor is slightly more advanced than its predecessor – it only encrypts a limited number of file extensions to keep the target computer’s CPU usage low and so try to avoid manual detection. Even if the power usage has been made more efficient in this version, it should still be noticeable in slower Startup and running speeds that may still result in occasional program crashes and screen freezing. Unasked for connection to the internet and busy port activity can sometimes be noticed as the malware tries to contact the C&C. And as there is no longer a server to contact, this should provide a clearer indication of infection to the user, as the ransomware will repeatedly attempt this.
If a system starts to run erratically in this way, a check of personal files for extension changes will confirm the malware at work. If detected, back-up all unaltered files to an external storage device and disconnect all internet and network connections. Place all corrupted files in a folder. Then remove Bitcryptor either manually or with an anti-malware program (see below for instructions). Due to certain defence mechanisms in the ransomware, it may be necessary to download any required software using another system and then introduce this via a disk or USB flash. When the system is completely cleared, install and run the decryption software, then have a serious think about how the ransomware gained access, and how to prevent further malware incursions.
How to prevent Bitcryptor
It’s important if plagued by one of these parasites to try to identify how they gained entry. Examine the methods above, and keep these in mind while browsing, sharing, downloading and installing. All routes for malware are preventable. Then there are ways to strengthen and secure an operating system. First, look at browsing; ensure that browsers are always the latest versions and that settings are adjusted to give maximum warning possible regarding compromised/hazardous ‘sites. Use controls to disallow any add-ons and extensions without consent and also regarding the use of cookies. Make sure that the operating system is current with any security patches/updates available.
To help prevent the accidental opening of disguised in-text links, disable the ActiveX function for all Microsoft Office applications. Install the best available firewall and set to disallow Tor and I2P connections – this can often stop malware running. Use the firewall’s settings to limit port use and cover all possible entries like wireless networks and Remote Desktop Protocol (which should be disabled if not used). Use the Microsoft ‘site for instructions on how to impose Administrator Privilege settings to stop executables running on certain file and registry paths (for example, Bitcryptor uses %AppData% and %LocalAppData% files and to block these using this setting will disable the ransomware). Install some good software that will regularly scan for malware.


hello every one
my computer infected by tesla crypt and all my file are crypt , and now all my file type are vvv . I think its vvv extinction file crypt . after the my malware program delete the virus .
now the problem is , I’m formatted my computer from win8 to win 10 , and I cant restore my file .
now please help me because I need my important file to do my work .
Hey Mustafa, I can not understand well: did you format your hard drive when you migrated from Windows 8 to Windows 10? Or just made an upgrade (without formatting)?
Thanks,
Daniel