I wrote this article to help you remove Crying Ransomware. This Crying Ransomware removal guide works for all Windows versions.
The Crying Ransomware is one of the newest members of the dreaded ransomware family. The parasite is related to another very dangerous threat – the HiddenTear ransomware – and if you are currently infected with it, you are in big trouble. There is a reason ransomware pieces to be considered the most notorious type of cyber infections. Their single purpose is to steal your money. Actually, “steal” is not the right word here. The Crying Ransomware doesn’t steal your money. It practically makes you give it voluntarily. As soon as the pest lands on board, it gets activated. The first thing the ransomware does is do perform a thorough scan of your machine in search for your private files. And when we say “files”, we mean all of your files.
It doesn’t take it long before Crying finds all of your pictures, videos, music, documents, work-related files, presentations, etc. Once it finds them, it encrypts them with a strong encryption algorithm. Thus, you are no longer able to open any of them. You still see their icons but you are not able to use them in any way. You probably have some very important data on your machine. Most people do. And now, it is encrypted.
The ransomware keep everything hostage and there is nothing you can do unless you have kept backups of your data. However, most users tend not to do that but it is the best way of winning the fight against ransomware. This pest takes your files for a reason. It is planning on blackmailing you for money. As soon as the file-locking process is over, you will see that your data has the “.crying” extension appended to it. Seeing this add-on means that it is time for the extortion step.
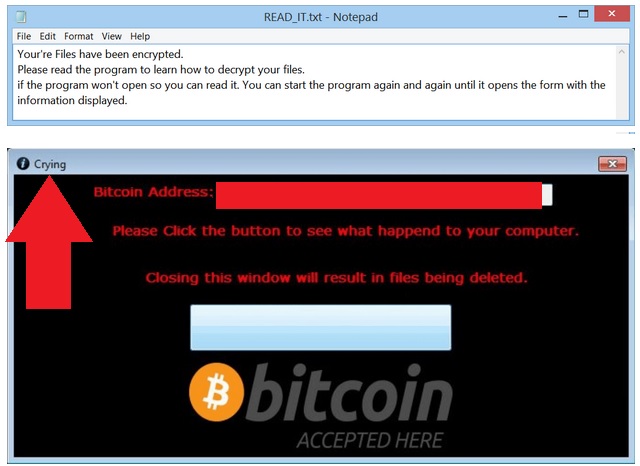
Crying encrypts your data for one reason only – to make you pay for a decryptor tool. Do you see why this cannot be called stealing? The pest relies on the fact that you have some crucially important information among the locked one and you will do anything to get it back. This is when the pest drops a note for you – a READ_IT.txt file and also launches a “Crying” program window. According to the note, if you want your files back you have to pay 0.5 Bitcoins (1376 USD at the moment). The hackers behind the ransomware claim that once you pay, they will send you a decryption tool and you will be able to recover your data. However, you have zero guarantees that crooks will keep their end of the bargain. Usually, they don’t. They just take victims` money and then ignore them. If you don’t want that to happen to you, do not pay.
Paying is not a solution. You cannot trust these people to send you the right decryption tool if they send you anything at all. One thing is guaranteed, though. By paying, you are sponsoring them and helping them expand their business and attack more innocent people. Also, if you use your machine to make the transfer, you are exposing your personally identifiable and financial information as well. And all of this for nothing. Don’t become crooks` sponsor and forget about paying. Instead, follow our removal guide at the end of this article and clean your PC from this pest. Then, once it is gone, try to recover your encrypted data.
Now that you see how dangerous ransomware is, don’t let yourself get infected again. You were fooled once, take measures to protect yourself and your computer. One of the most popular methods which ransomware infections use to sneak in is spam email messages. Crooks send the parasite directly to your inbox in an email, disguised to look as a legitimate one. Don’t be gullible and don’t open messages from people you don’t know as, more often than not, they deliver infections.
Other infiltration tactics include freeware/shareware bundles, fake updates, exploit kits, corrupted pages/torrents, third-party ads, etc. A ransomware can even use the help of a Trojan horse to get it which means that you may have more than one infection on board. Get yourself a reliable anti-malware program, keep it up to date and regularly scan your machine to be sure it is infection-free.
Crying Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, Crying Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Crying Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

