I wrote this article to help you remove CRBR Ransomware. This CRBR Ransomware removal guide works for all Windows versions.
CRBR ransomware is a reincarnation of Cerber ransomware. Win-lockers inflict great damage on the targeted computer. They lock most files on the hard disk drive. CRBR ransomware encrypts a wide range of formats, a total of 493. The malevolent program appends a custom suffix to the objects it encrypts. It consists of four hexadecimal characters. They are generated at random which means that every instance of infection is associated to a different appendix. The purpose of the win-locker is to raise revenue for its developers. The insidious program demands a payment which is referred to as a ransom. The hackers promise to decrypt your files and uninstall the win-locker when you pay.
CRBR ransomware is distributed like most win-lockers. The secluded program travels inside spam emails. Researchers have found that the payload of CRBR ransomware consists of three executable files. Their names are generated in a specific way. The first is given a random number as a title. The name of the second is comprised of three random which are all the same. The third is named like the custom extension mentioned earlier. It receives a title which consists of several random letters and numbers. In addition, CRBR ransomware drops two .dat modules called read.php and user.php. The entire is packed with an attachment. The sender will try to convince you that the fake notification is legitimate. He will describe the supposed document as important and urge you to open it. In many cases, spammers write one behalf of existing companies and organizations. To confirm that a given letter is genuine, look up the email addressed the sender has used to contact you.
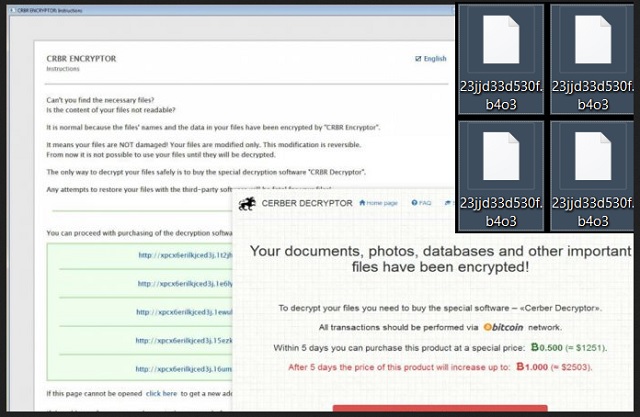
CRBR ransomware deploys a combination of RSA-512 and RC4 algorithms to lock files. The virus renders the coding schemes of the targeted objects by replacing blocks of data. It produces a set of a public and private RSA key. The former encrypts files, while the latter can be used to decrypt them. This is what the ransom is for. When CRBR ransomware has finished locking your personal files, it will drop a message on your desktop to notify you of its actions. It produces a couple of documents titled _R_E_A_D___T_H_I_S___[ID]_.txt and _R_E_A_D___T_H_I_S___[ID]_.hta. The sinister program assigns a unique identifier number to each victim.
The first of the latter is referred to as a ransom note. The creators of CRBR ransomware explain the situation in detail. They notify users that their documents, photos, databases and other important files have been encrypted. This particular line has been saved into a synthetic voice recording. It is played after completing the encryption. CRBR ransomware requires victims to pay the ransom in Bitcoins. The amount has been set to change after the first 5 days. If you comply by then, you will have to pay 0.6773 BTC. After the initial period, the ransom will increase to 1.3546 BTC, or double the original amount. The cyber criminals have given an approximation as to how much the ransom convert to. It should be noted that this information is outdated. The exchange rate for Bitcoins has increased over time. The ransom currently amounts to $1754.15 USD and $3,508.31 USD, accordingly.
After you pay the ransom, you will receive a private key. By entering it into Cerber Decryptor, you should be able to unlock your files. Of course, there is no official agreement. You have to trust the owners of the win-locker. This would be a risky move. The renegade developers are not obliged to provide the decryption key. Since their actions are illegal, they have taken measures to protect their identity. As we already established, the ransom needs to be paid in Bitcoins. This cryptocurrency is secure. The transaction cannot be traced by third parties. The payment website is hosted on the Tor network. This protects the geographic coordinates of the cyber criminals. It is best to try to recover your data on your own. For the purpose, you can use one of the free tools listed below.
CRBR Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, CRBR Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since CRBR Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

