I wrote this article to help you remove Aleta Ransomware. This Aleta Ransomware removal guide works for all Windows versions.
Aleta is one of the newest additions to the already pretty huge ransomware family. It is an improved and updated version of the well-known BTCWare infection. Like all ransomware pieces, Aleta`s goal is your money. The pest enters your machine behind your back and then encrypts everything that you have stored on your PC. First, it performs a thorough scan to locate all of your private information and then it locks it with a strong encryption algorithm. Thus, the ransomware denies you access to your own files.
You cannot see your pictures anymore. You cannot listen to your music. You cannot edit your documents. You have no access to any of your files whatsoever. And all of this happens in silence. You don’t realize there is a notorious parasite on board until you that your data in no longer accessible. The infection doesn’t ask for your permission to encrypt. It acts and you only see the results. For example, one day you turn on your machine only to see that all of your files have a brand new extension appended to them. The “email.[black.mirror@qq.com].aleta” extension which you don’t remember adding. Of course, you don’t. Seeing your data renamed like this means that the encryption process is over and Aleta keeps all of your files hostage. You know what is next, don’t you?
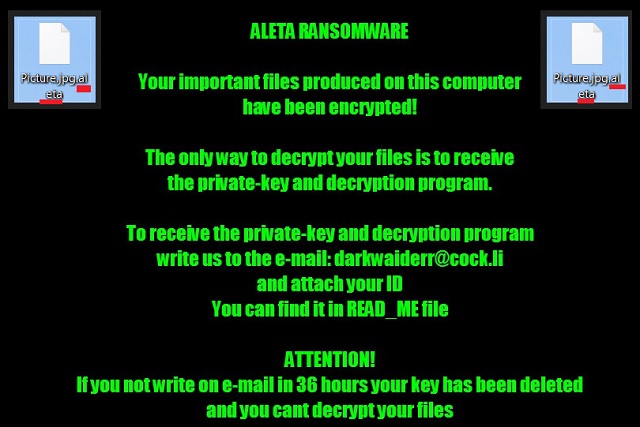
Once the encryption is complete, the ransomware drops a note for you. That’s the ransom note and it is named !#_READ_ME_#!.inf. This message explains your situation and provides instructions on how to get your files back. Unsurprisingly, this process involves money. The crooks demand 2 Bitcoins from you which equals to nearly $5000. They promise that if you pay, they will send you a special tool to decrypt your data. Of course, this is a lie. Cybercriminals cannot be trusted. They would say practically anything to get you to give them money. Don’t fall for that trap. There is no guarantee that you will actually receive what you pay for.
Once they receive the payment, hackers tend to ignore their victims. Don’t be one of these victims. Don’t give these crooks even a cent of your money as you will end up double-crossed. Not to mention that by paying, you will be sponsoring their business and also exposing your private information to them. Don’t. Dealing with crooks is dangerous and it won`t end well for you. What you need to do is remove Aleta from your machine ASAP and then try and safely recover your data. Don’t decrypt your files while the ransomware remains on board as they can be re-encrypted hours later. You need to clean your machine first and our removal guide at the end of this article can help you do that.
How did Aleta enter? Usually, ransomware travels the web via spam email messages and their malicious attachments so proceed with caution whenever you receive an email from an unknown sender and whatever you do, don’t download the attached files. Other popular infiltration methods include corrupted pages and malicious third-party ads. A ransomware can be disguised as a program update as well or hitch a ride with a bundle.
Last but not least, ransomware gets distributed via exploit kits and the help of Trojan horses. There are many, many tactics and it is your job to protect your machine. Be more vigilant and don’t give into haste and distraction. Hackers pray for your carelessness. None of the above-mentioned methods would work without it. Also, download a reliable anti-malware program, keep it updated and regularly scan your computer for intruders. And one last piece of advice, always keep backups of your most important files. This way you would know they are safe if you ever get infected with such an infection again.
Aleta Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, Aleta Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Aleta Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

