I wrote this article to help you remove ViACrypt Ransomware. This ViACrypt Ransomware removal guide works for all Windows versions.
ViACrypt ransomware is a win-locker virus which appears to have been developed in Latvia. The payment website of the clandestine program contains instructions in Latvian. Apart from this, the parasite lists information in English. Upon entering your computer and inflicting the damage it is scheduled to, it will drop a couple of files on the desktop: your_encryption_public_key.rkf and your system has been encrypted! please read further instruction!.txt. The first, as indicated, is the public encryption key. This is the object which has infected your personal data. The second is a standard component called a ransom note. Its purpose is to explain what has happened and push the victim to pay the cyber criminals.
ViACrypt ransomware uses RSA-1024 cryptography to lock files. This is an asymmetric algorithm. Cryptosystems are divided into symmetric and asymmetric. To make the situation as inconvenient for the victim as possible, the nefarious program targets a wide range of formats. It will render all your important data inaccessible. The target range of ViACrypt ransomware encompasses text documents, spreadsheets, presentations, databases, images, videos, audios, compressed archives, zip folders and others. The win-locker appends the .via suffix to the names of the infected objects.
Malware researchers have yet to discover how much the creators of ViACrypt ransomware ask from their victims. People have to contact the renegade developers before receiving further information regarding the payment. The ransom note lists a set of steps you must take. First, you have to enter the payment website. The next task is to upload the public encryption key to the platform. The remaining steps are to be completed after getting a response. The hackers will tell you how much the ransom is and guide you through the payment process. The amount of the ransom is not known as this point in time. Another important aspect is how the sum is transferred. We can only assume the cyber thieves have taken measures to make the transaction secure, since they have done so for the payment website.
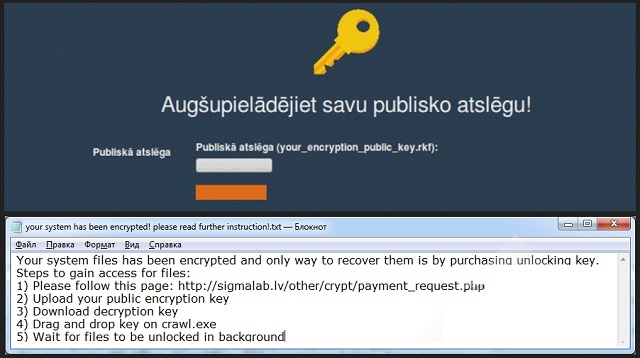
ViACrypt ransomware has a specific algorithm in terms of the decryption procedure. Once you have completed the payment, you will need to download the decryption key. Afterwards, you will have to drag and drop the key on a file called crawl.exe. This will trigger a background process which will unlock the encrypted files. Different win-lockers have different algorithms. Most of them provide a decryption tool. Others have a decrypter built in. ViACrypt ransomware unlocks files in an unusual way. Another uncommon characteristic about the insidious program is that it does not use the Tor browser to host the payment website. This is the choice for most win-lockers because it protects the geographic location of the hackers when they receive the ransom money.
Our advice to users who have contacted ViACrypt ransomware is not to pay the ransom. You should not communicate with the hackers at all. The authors of the win-locker are criminals. They cannot be trusted to make good on a proposed deal. There are many documented instances where ransomware developers have not decrypted people’s files after receiving the ransom. Another potential risk is to suffer another attack. While the decryption key will unlock your files, it will not uninstall the rogue program. The hackers can launch a second attack. It is best to restore your data on your own. For the purpose, you can use one of the free tools we have listed below. Note that they will only work if the shadow volume copies of your files are intact. The win-locker may have deleted them.
To protect your system from malware, you have to keep your guard up at all times. There are many ways for infections to penetrate your machine. ViACrypt ransomware uses spam emails. This is a common propagation vector. The payload of the furtive program travels hidden behind attachments. The host file will be presented as an important document, like a recommended letter, a bill, a fine, an invoice, a notice, a subpoena or something else. A spammer can devise a fake message to resemble a genuine notification from an existing organization. Citing a legitimate company or legal entity can make the bogus message believable. To check whether a given email is truthful, proof the account it was sent from.
ViACrypt Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, ViACrypt Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since ViACrypt Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

