I wrote this article to help you remove CryptoGod Ransomware. This CryptoGod Ransomware removal guide works for all Windows versions.
The Web is full of malicious infections. And yet, there is a certain type that stands out and is considered the worst possible parasite you can encounter. That’s ransomware. These file-encrypting parasites totally deserve their horrible reputation. Unlike other infections which try to steal your money, ransomware uses a different technique. It takes something of yours and them extorts you for money. It practically makes you pay voluntarily. This is why these infections are so dreaded. And CryptoGod is one of them. Named after an Indonesian metal band, this virus is said to be another version of the MoWare H.F.D. infection, which, in turn, is related to the HiddenTear ransomware project. Either way, you are stuck with an extremely dangerous parasite and you have to take measures. The most important thing is not to panic. If you do, you won’t be able to think clearly and may act impulsively. Needless to say, this won`t end well for you. Take a few minutes to read this article and get a clear view of your situation.
As a classic ransomware, CryptoGod follows a standard pattern. First, it enters your machine in silence. The most common infiltration method used by ransomware is spam email messages. CryptoGod gets executed via an .exe file named Ricevuta 25-05-2017. Usually, this file gets sent to you in a seemingly legitimate message and if you open it, you let the ransomware lose. Be extra careful when you receive emails from unknown senders. Even if the look safe and even helpful, they are probably corrupted and deliver infections. Don`t open them but delete the straight away. Hackers are smart. They don’t send a message which says “Dangerous Ransomware” is a big neon sign. They disguise the emails and make them seem reliable. Like a job application or a shipping invoice. Be smart. Other entering techniques include freeware bundles, fake updates, exploit kits, the help of a Trojan horse, corrupted pages, etc. Don’t let yourself be fooled by crooks. Choose vigilance over negligence and keep your machine clean.
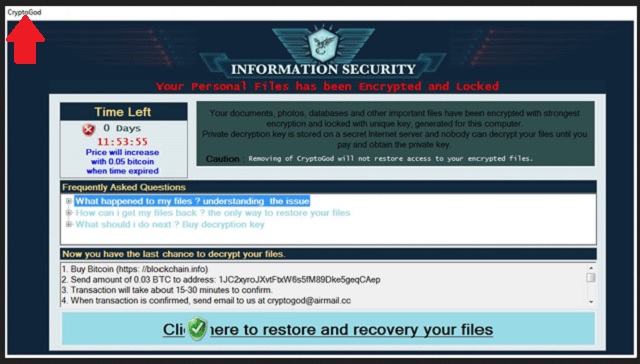
Once on board, CryptoGod doesn’t waste time but proceeds with the encryption. First, it scans your machine searching for your private files. Of course, it doesn’t take long before it finds everything. And by everything, we really mean everything. All of your pictures, videos, music, presentations, MS Office files, other documents, etc. get locked with the AES encryption algorithm. The ransomware encrypts them, thus making them inaccessible to you. The pest even renamed the locked data by adding the “.payforunlock” extension to each file. Seeing this add-on means that the encryption process has been completed and your files are effectively locked. You see their empty icons but you cannot use them in any way. Your PC is unable to read them anymore due to their new format. This is the moment when CryptoGod makes its final move. The extortion. It drops a note for you which states that if you want your data back, you have to pay a ransom to receive a decryption key.
The hackers demand 0.03 Bitcoins. Yes, it is not a lot but you still should pay. Why? Because paying doesn’t give you any guarantees. And neither does dealing with crooks. They may not keep their end of the deal. And usually, they really don’t. They just take your money and ignore you. They goal is money. Your files are not their concern. So, think carefully before doing anything. Keep in mind that using your machine to pay the ransom gives crooks access to your personal and financial credentials. Also, the money you give them will be used for nothing but business expansion and more malware creation. This is not a solution. Take matters into your own hands. Delete CryptoGod manually by using our removal guide below and keep your Bitcoins. Once your machine is clean, safely try to recover your locked data. And a piece of advice for the future, download a good anti-virus program to help you fight cyber infections. Also, backup your most valuable files so you are sure they are safe.
CryptoGod Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, CryptoGod Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since CryptoGod Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

