I wrote this article to help you remove Resurrection Ransomware. This Resurrection Ransomware removal guide works for all Windows versions.
The Resurrection ransomware is the nth member of the dreadful ransomware family. According to experts, this infection is a descendant of the HiddenTear project and it is dangerous. Not because it is related to and inspired by HiddenTear, but simply because it is a ransomware. Pretty much all infections of this type operate the same way. If you have seen one of them, you have seen all of them. So, Resurrection follows the standard pattern. Invade, Encrypt, Extort. That’s it. The pest enters your machine mostly via malicious spam email messages which are disguised to look like legitimate ones. Here comes your part. You should not open emails from unknown senders. We know you have heard that a hundred times already, but hear it once again.
If you receive a strange email from a person you don’t know, ignore it or at least proceed with caution. The same goes for emails which start with “Dear Customer” and “Dear Friend” and claim to be sent by a well-known organization. Before doing anything else, check the sender. Visit this company`s official page and see if their address matched the one you received the message from. If not, you know what to do. It is crucial that you are always careful. Not only with spam emails, though. There are other techniques as well like fake program updates, corrupted pages, freeware bundles, malicious ads, etc.
As soon as the pest tricks you into allowing it to enter, it proceeds with the file-encryption. First, the ransomware scans your machine in search for your private files. All of your private files. We are talking pictures, videos, music, presentations, MS Office documents, and so on and so forth. All of them fall victims to the ransomware and become inaccessible to you. You cannot open them, listen to them, edit them. Nothing. They are locked and beyond your reach. The infection also changes their format by adding the “.resurrection” extension to each one. Seeing your data renamed like this means that the encryption process is over. Resurrection turned them into unusable gibberish. Needless to say, seeing your valuable data like this make cause you to panic very quickly but it is important to stay calm. The hackers want you to be scared and not thinking clearly. This way you will be more willing to comply with their demands.
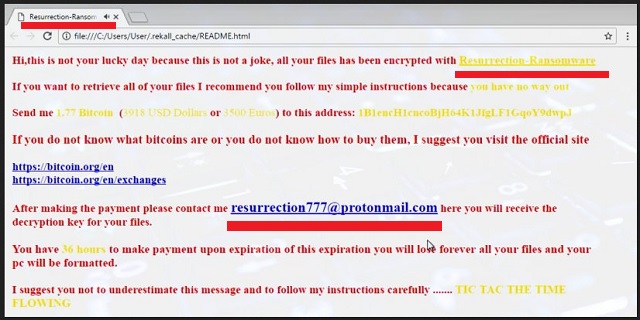
Speaking of their demands, once the file-locking process is over, Resurrection drops the README.html file in all folders that contain encrypted data. This file is the ransom note, according to which, you have to pay 1.77 Bitcoins (4,820 at the moment) if you want your files back. Yes, that is a lot of money to spend on your OWN files. The hacker claim that once you pay, they will send you a special decryption tool to recover your data. They provide the resurrection777@protonmail.com email address for you to contact them for further details. Don’t get in touch with them. Don’t fall into their trap. These people only care about money and they hope that you will be panicked enough to act impulsively and pay. The html file even plays a dramatic music which reminds the Happy Potter soundtrack only to bring more suspense to the situation.
Don’t give into fear. Paying is not a solution. And do you know why? Because it guarantees you nothing. You cannot rely only on the hackers` word. They were the ones to lock your data in the first place. What makes you think they will keep their end of the bargain and give you a decryptor? There is a good chance they don’t. Besides, even if they do give you the tool, it doesn’t remove the ransomware. It only unlocks your file but they can be re-encrypted hours later. Why risk it? Also, by paying you are exposing your private information to crooks. Needless to say, this won`t end well for you. Forget about giving them money. Instead, use our removal guide below and remove Resurrection for good. Then, proceed with the guide and try retrieving your data. But in the future, it would be best if you keep backups of your most important files.
Resurrection Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, Resurrection Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Resurrection Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

