I wrote this article to help you remove Thunder Crypt Ransomware. This Thunder Crypt Ransomware removal guide works for all Windows versions.
Thunder Crypt ransomware is a virus which encrypts files. The other term for this type of infection is win-locker. Upon entering a computer, Thunder Crypt ransomware scans all of its fragments in search of vulnerable objects. The target list includes Microsoft Office documents, Adobe documents, images, audios, videos, zipped folders, compressed archives, logs and others. The encrypted objects have a custom extension appended to their original names. It has yet to be reported whether the suffix is the same in every case or it is generated at random for each instance of infection. The win-locker targets files from different directories. It only excludes the system folders because they contain components which the OS needs in order to run properly.
Like the majority of win-lockers, Thunder Crypt ransomware is distributed by means of spam email campaigns. The fake message can be on different topics. In most cases, the spammer states that the matter is urgent. The goal is to have the recipient open an attachment before thinking it through. The attached file will transfer the payload of Thunder Crypt ransomware onto your hard disk drive. You should filter your in-box messages. To check whether a given email is genuine, proof the contacts. If the notification legitimately comes from a certain company or entity, the correspondent would have used an official account to contact you. You can visit the organization’s website for reference.
Thunder Crypt ransomware locks files by rendering their code scheme. For this purpose, the sinister program uses advanced cryptography. The renegade developers have chosen AES-2048 which stands for Advanced Encryption Standard with 2048-bit rate. This cryptosystem is used by many win-locker viruses. It has proven to be effective. Thunder Crypt ransomware will render your computer useless within minutes. The malignant program runs its processes on the background which makes it near impossible to detect and disable on time.
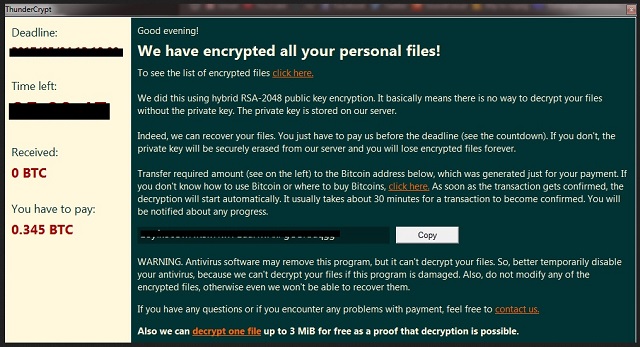
Upon completing the encryption, Thunder Crypt ransomware displays a message to inform the victim what has occurred. The nefarious program explains what it has done and for what purpose. The note begins like a regular message which goes to show how audacious cyber criminals can be. They greet their victims before explaining the situation. Thunder Crypt ransomware is used to make proceeds at the expense of PC users. The creators of the win-locker make the bold demand of requiring people to pay for regaining access to their rightfully owned data.
Thunder Crypt ransomware generates a public key for encrypting files. A private key is required to unlock them. The fraud artists ask for a ransom of 0.345 Bitcoins in exchange for it. This converts to $556.04 USD as per the current exchange rate. Victims have to transfer the sum to a Bitcoin wallet, listed in the note. The hackers give a deadline of 24 or 48 hours. There are two versions of Thunder Crypt ransomware which only differ in terms of the deadline. The remaining time is measured by a countdown clock, embedded within the notification window.
To prove that they have created a working decryption key, the authors of Thunder Crypt ransomware give victims the chance to have one file decrypted for free. The user gets to choose which file will be restored, but there is a restriction. It can be up to 3 MB in size. To prevent people from removing the virus on their own terms, the coders have included a warning message in the ransom note. They state that if you damage Thunder Crypt ransomware, the decryption would not be possible to perform. For this reason, they advise against using an antivirus program in the attempt to remove the win-locker.
You should not pay the owners of Thunder Crypt ransomware or any other virus developers. Cyber criminals cannot be trusted. There have been many instances where victims did not have their files restored after paying the ransom. Another possible occurrence is for the hackers to launch another attack after unlocking your files. Performing a decryption does not equal removing the program. The best course of action is to uninstall the win-locker with the use of an antivirus utility and proceed to recover your files from their shadow volume copies.
Thunder Crypt Ransomware Removal
Method 1: Restore your encrypted files using ShadowExplorer
Usually, Thunder Crypt Ransomware deletes all shadow copies, stored in your computer. Luckily, the ransomware is not always able to delete the shadow copies. So your first try should be restoring the original files from shadow copies.
- Download ShadowExplorer from this link: http://www.shadowexplorer.com/downloads.html.
- Install ShadowExplorer
- Open ShadowExplorer and select C: drive on the left panel

- Choose at least a month ago date from the date field
- Navigate to the folder with encrypted files
- Right-click on the encrypted file
- Select “Export” and choose a destination for the original file
Method 2: Restore your encrypted files by using System Restore
- Go to Start –> All programs –> Accessories –> System tools –> System restore
- Click “Next“

- Choose a restore point, at least a month ago
- Click “Next“
- Choose Disk C: (should be selected by default)
- Click “Next“. Wait for a few minutes and the restore should be done.
Method 3: Restore your files using File Recovery Software
If none of the above method works, you should try to recover encrypted files by using File Recovery Software. Since Thunder Crypt Ransomware first makes a copy of the original file, then encrypts it and deletes the original one, you can successfully restore the original, using a File Recovery Software. Here are a few free File Recovery Software programs:

