Computer users should beware of a new encryption virus called CHIP ransomware and its distribution host, the RIG-E exploit kit. The discovery was made by Brad Duncan of the threat intelligence analyst team for Palo Alto Networks Unit 42. Mr. Duncan published an article last Thursday to alert people of the virus threat.
The researcher was able to track the propagation pattern of CHIP ransomware down to the RIG-E exploit kit. An exploit kit (EK) is a malicious program which looks for vulnerabilities in the operating system (OS) it penetrates. If it manages to find sufficient vulnerabilities, it downloads and installs the payload to the targeted computer. Over the past few months, the RIG-E EK has become a prominent host for many infections.
Upon doing a thorough examination on CHIP ransomware, security experts uncovered the technical specifications of the virus. CHIP ransomware utilizes AES encryption algorithm to lock files. Then it proceeds to encrypt the AES key with a unique RSA-512 cipher, downloaded from the command and control (C&C) server of the hackers.
The encrypted files are marked with the custom file extension .CHIP. It is appended after the original extension. The icons of the infected items are changed to the default blank icon, used to signify an unfamiliar file format.
Like most win-lockers, CHIP ransomware informs victims of its actions via a ransom note. The file is titled CHIP_FILES.txt. It explains the situation, notifying the person that his files have been rendered inaccessible and telling him what he needs to do to have them decrypted.
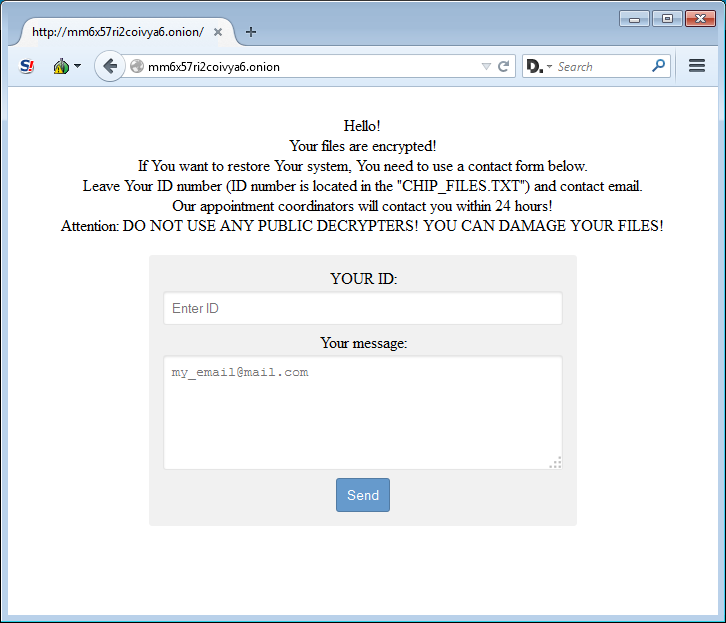
CHIP ransomware uses the TOR web browser to collect payments from affected users. This program allows the cyber criminals to protect their identity and their coordinates. A link to a payment page is provided in the ransom note. The virus creates a unique support home page for each user.
The TOR home page does not provide full instructions on the payment process. Users are required to contact the developers of the rogue program to receive them. They are prompted to enter their ID (as listed in the ransom note) and leave a message which should contain their email address. The people behind CHIP ransomware contact victims within 24 hours upon receiving their message.
The ransom the creators of CHIP ransomware ask for is yet to be documented. While malware experts work on creating a custom decrypter, users need to be careful not to contact the RIG-E EK which can get them infected with the virus.

