A bug can exploit the macOS High Sierra to gain root access to the system without entering any password. Since the remote exploitation is also possible, users expect that Apple will release a patch very soon.
Since the appearance of High Sierra, some users have complained that after updating the operating system their admin accounts had turned into standard ones.
On November 13, one user on the Apple’s Developer Forums suggested logging in with “root” and no password in order to obtain an access for creating an admin account. However, a week later, it turned out that logging into the root account with no password should not be possible and that this is a major vulnerability.
To gain root access via the above-mentioned vulnerability, requires entering the “root” username in the graphical user interface (GUI) and leaving the password field blank. According SecurityWeek, this is quite easy for reproducing, though a couple of attempts are needed.
Hackers just have to access “System Preferences” from the Apple menu and click on any of the categories which require administrator privileges in order to make changes (e.g. Security & Privacy, Users & Groups, Parental Controls).
After that they should click on the lock icon in the bottom left corner of the window and enter the username “root” with a blank password when prompted. Then, press the Enter key or the Unlock button twice and the root access is granted.
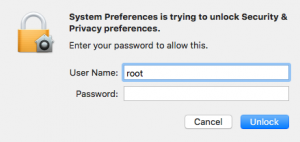
After analyzing the vulnerability, the experts reported that an attempt to log in as root with a blank password activates a subroutine that creates the root account, which Apple has disabled by default. When the root account has been activated, logging in as root with no password works at once.
Additionally, the macOS hacker Patrick Wardle and his colleagues have managed to reproduce the flaw remotely as well if sharing services are enabled on the device.
Security researchers warned that hackers could be scanning the Web for remotely accessible computers which they can attack using the macOS flaw.
Currently, Apple is working on patching the vulnerability. Meanwhile, users can protect themselves against potential attacks by manually setting a password for the root user. Disabling sharing services is also a good way for preventing remote exploitation of the security hole.

